Picture this: You're a security analyst drowning in alerts, reports and threat feeds. Every day, thousands of new indicators, threat actor profiles, and attack patterns flood your systems. Sounds familiar? 😅
What if your AI assistant could actually understand the complex web of cybersecurity information and give you answers that truly connect the dots?
We've been experimenting with a combination that's changing how we interact with threat intelligence: GraphRAG and OpenCTI. Instead of just searching for keywords in documents, this approach navigates the interconnected world of cyber threats the way an experienced analyst would - following relationships, understanding context, and delivering insights that actually make sense.
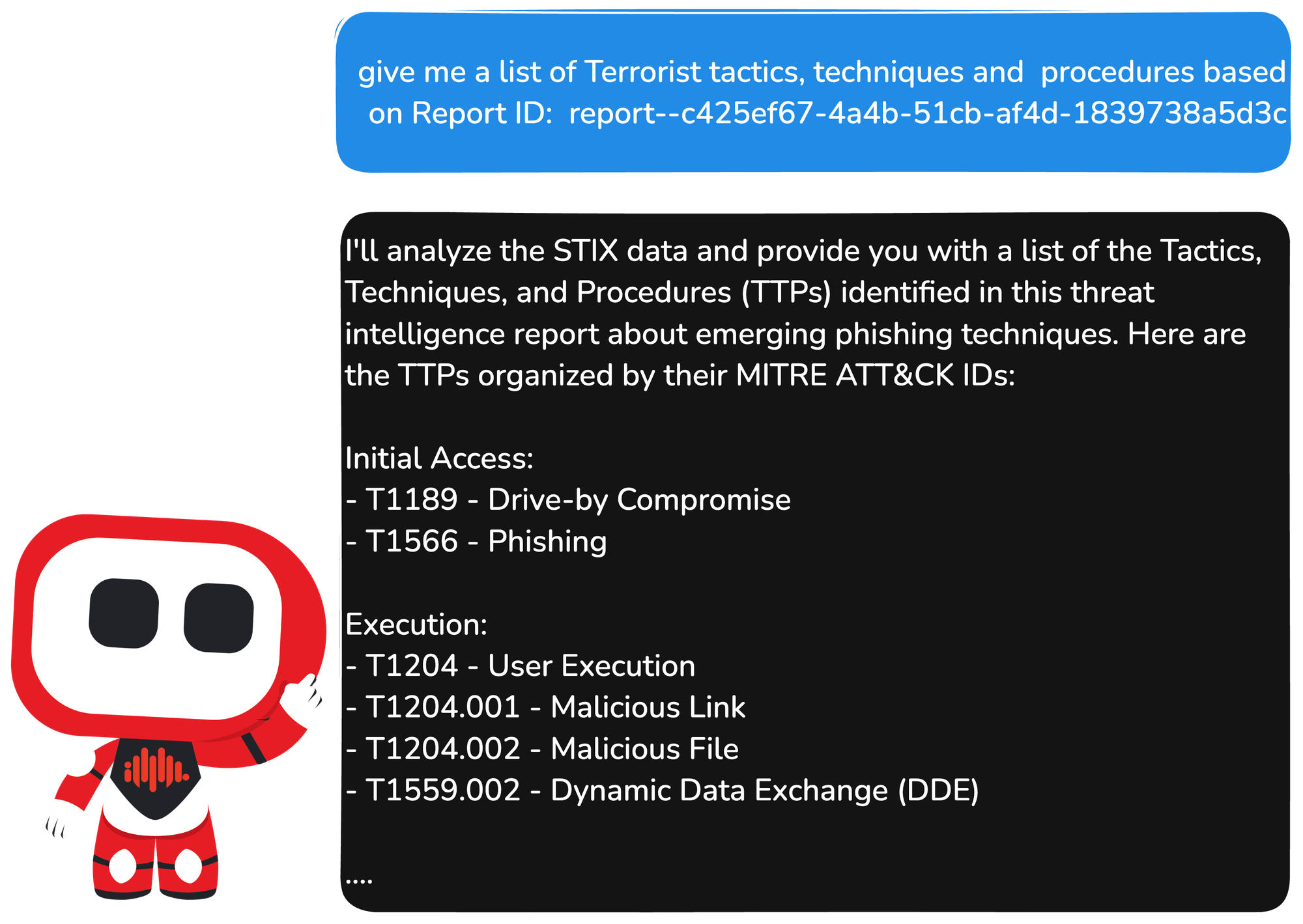
In this article, we will walk you through how combining graph-based knowledge with modern AI techniques can transform your cybersecurity intelligence capabilities. Whether you're seasoned security professional or just getting started with threat intelligence, you'll find something valuable in this practical approach to making AI truly understand the complex world of cyber threats.
Real Case Scenario: Building a Personal AI Cybersecurity Assistant
To demonstrate the practical application of GraphRAG with OpenCTI, we've implemented a personal AI assistant that leverages the graph-based knowledge representation in OpenCTI to provide enhanced cybersecurity intelligence.
GraphRAG
GraphRAG represents an evolution in the field of Retrieval Augmented Generation, specifically designed to work with graph-based knowledge structures. Unlike traditional RAG systems that primarily work with document-based knowledge, GraphRAG can navigate and reason over interconnected data points.
Key Components of GraphRAG
- Graph Knowledge Representation: Data is stored as nodes (entities) and edges (relationships), enabling complex relationships to be captured and traversed.
- Graph-aware Retrieval: The retrieval mechanism considers not just individual data points but the connections between them, allowing for context-rich information retrieval.
- Graph-enhanced Generation: The language model receives both the retrieved information and the structural context from the graph, resulting in more nuanced and comprehensive responses.
- Knowledge Graph Navigation: The ability to follow connections between entities enables more sophisticated reasoning paths and knowledge discovery.
OpenCTI
OpenCTI (Open Cyber Threat Intelligence) is an open-source platform designed to organize, store, analyze, and visualize threat intelligence information. It provides a comprehensive knowledge base for cybersecurity professionals to manage CTI data and collaborate effectively.
Key Features of OpenCTI
- Graph-based Data Model: OpenCTI uses a graph database to represent cyber threat intelligence, capturing complex relationships between threats, actors, tools, and techniques.
- STIX2 Compliance: The platform adheres to Structured Threat Information Expression (STIX2) standards, ensuring interoperability with other threat intelligence platforms.
- Connectors Ecosystem: OpenCTI provides various connectors to integrate with external data sources and tools, enabling automated data ingestion and enrichment.
- Visual Analytic: The platform offers powerful visualization capabilities to help analysts understand relationships and patterns in threat intelligence data.
Implementing GraphRAG with OpenCTI
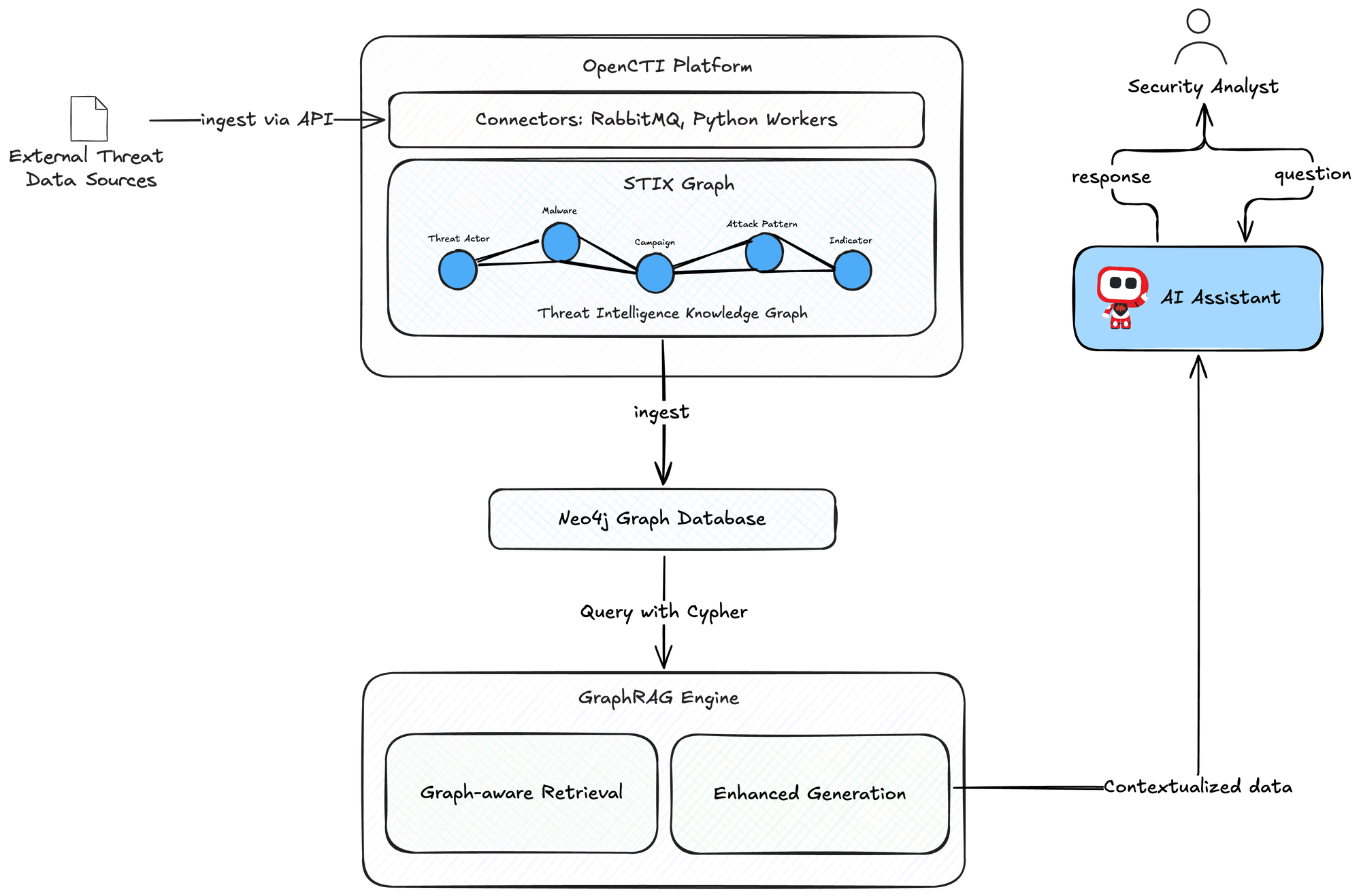
Combining GraphRAG with OpenCTI offers a powerful approach to cybersecurity intelligence that leverages the strengths of all these technologies.
A. Data Extraction and Processing
The first step involves extracting relevant data from OpenCTI's graph database. This includes:
- Threat actors and their attributes
- Malware profiles and capabilities
- Attack patterns and techniques
- Indicators of compromise
- Relationships between these entities
B. Graph Knowledge Representation
The extracted data is transformed into suitable graph representation for the GraphRAG system. This involves:
- Defining entity types and their properties
- Establishing relationship types between entities
- Preserving contextual information within the graph structure
C. Retrieval Mechanism Design
The retrieval component of GraphRAG needs to be customized for cybersecurity intelligence:
- Implement graph traversal algorithms to follow relevant relationships
- Design query transformation techniques to convert natural language queries into Cypher queries for Neo4j
- Develop relevance scoring methods specific to cybersecurity contexts
- Utilize Neo4j's path-finding algorithms to discover hidden connections between threats
D. Generation Enhancement
The generation component needs to effectively utilize the graph-based knowledge:
- Provide context-aware prompts that include graph structural information
- Implement techniques for explaining reasoning paths through the knowledge graph
- Develop methods for handling uncertainty and conflicting information
Why This Is a Game-Changer for Security Teams?
The Good Stuff
See the Big Picture, Not Just the Pieces When your AI assistant can navigate the web of connections in OpenCTI's graph structure, it doesn't just see isolated security incidents—it understands how everything fits together. This means you get answers that actually make sense in the real world of cyber threats.
Connect the Dots Like Never Before Let's face it: traditional document searches miss a lot. With graph-based reasoning, your AI can spot patterns and connections that would otherwise slip through the cracks. "This malware looks similar to what we saw targeting financial institutions last month" becomes a natural observation rather than a lucky find.
Get Answers You Can Actually Use No more generic security advices. With structured threat intel feeding your AI, you'll get specific, actionable responses tailored to your situation. Need to know how to defend against a particular threat actor's TTPs? The system pulls precisely what you need.
Always Up-to-Date Without the Hassle As soon as new threat intel hits your OpenCTI instances, your AI assistant knows about it. No waiting around for model retraining or knowledge updates—it's like having an analyst who reads everything the second it comes in.
The Tricky Parts
Garbage In, Garbage Out Your AI is only as good as the data in your OpenCTI instance. Incomplete data or missing connections will lead to blind spots in your security posture. You'll need solid data hygiene practices to keep things running smoothly.
Some Questions Are Just Hard Turning a security analyst's complex question into the right graph query isn't always straightforward. "Show me all the techniques this threat group might use to target our industry" requires some serious behind-the-scenes magic to translate properly.
Keeping Things Speedy Graph operations can get resource-hungry fast, especially when you're working with large threat intelligence databases. You'll need to optimize if you want to quick responses rather watching the spinning wheel of doom.
Locking Down Sensitive Intel Your threat intelligence might contain sensitive information about vulnerabilities, incidents, or even your own security gaps. Strong access controls are non-negotiable here.
What's Next on the Horizon?
Automation That Actually Helps Imagine your GraphRAG + OpenCTI setup triggering the right response playbooks automatically. "We've detected activity matching APT29's latest campaign" could kick off targeted defense measures without waiting for human review.
Bringing All Your Intel Sources Together OpenCTI is just the beginning. Future systems could pull from multiple intelligence sources, giving you truly comprehensive view of the threat landscape that combines open source, commercial, and internal intelligence.
Security AI That Shows Its Work The best security decisions come with receipts. Enhanced explainability features would let analysts see exactly why the AI made a particular recommendation, building trust and improving decision-making.
Bottom Line
Combining GraphRAG with OpenCTI is a practical approach that gives us superpowers. By leveraging the rich connections in graph-based threat intelligence, AI security assistant can provide context-aware, actionable insights that actually help protect organizations. As these technologies mature, expect them to become essential tools in the security team's arsenal.

