Contributed by Lalu Raynaldi Pratama Putra.
One of the threats identified by IntelliBroń Orion is malware activities. The threat detector engine retrieves data from two different sources at the moment: network and host. IntelliBron employs at least two methods to detect malware activities from the network: signature-based and AI-based.
This article demonstrates how the IT professionals and analyst can swiftly identify and assess incidents indicating that an asset has been compromised by DarkCrystal RAT using Bellatrix Dashboard, an intuitive dashboard designed for IT professionals and analysts.
DarkCrystal Traffic Analysis
Type : Stealer,RAT
Analysis Summary
DCRat, a Russian backdoor, was initially introduced in 2018 but rebuilt and relaunched a year later. The DCRat backdoor appears to be the product of a single threat actor who goes online with the pseudonyms of "boldenis44", "crystalcoder" and Кодер ("Coder").
DCRat is one of the cheapest commercial RATs. For a two-month membership, the price starts at 500 RUB (less than 5 GBP/US $6), and it periodically drops even cheaper during special offers. This is written in .NET and features a modular structure, allowing affiliates to create their plugins using DCRat Studio, a dedicated integrated development environment (IDE).
The malware's modular architecture allows it to be extended for a variety of nefarious objectives, including surveillance, reconnaissance, data theft, DDoS attacks, and arbitrary code execution.
The DCRat consists of three parts: The malware comprises a stealer/client executable, a command-and-control (C2) endpoint/interface in the form of a single PHP page, an administrator tool, and is still in development.
The author announces any news and updates through a dedicated Telegram channel with approximately 3,000 users.
Bellatrix Dashboard
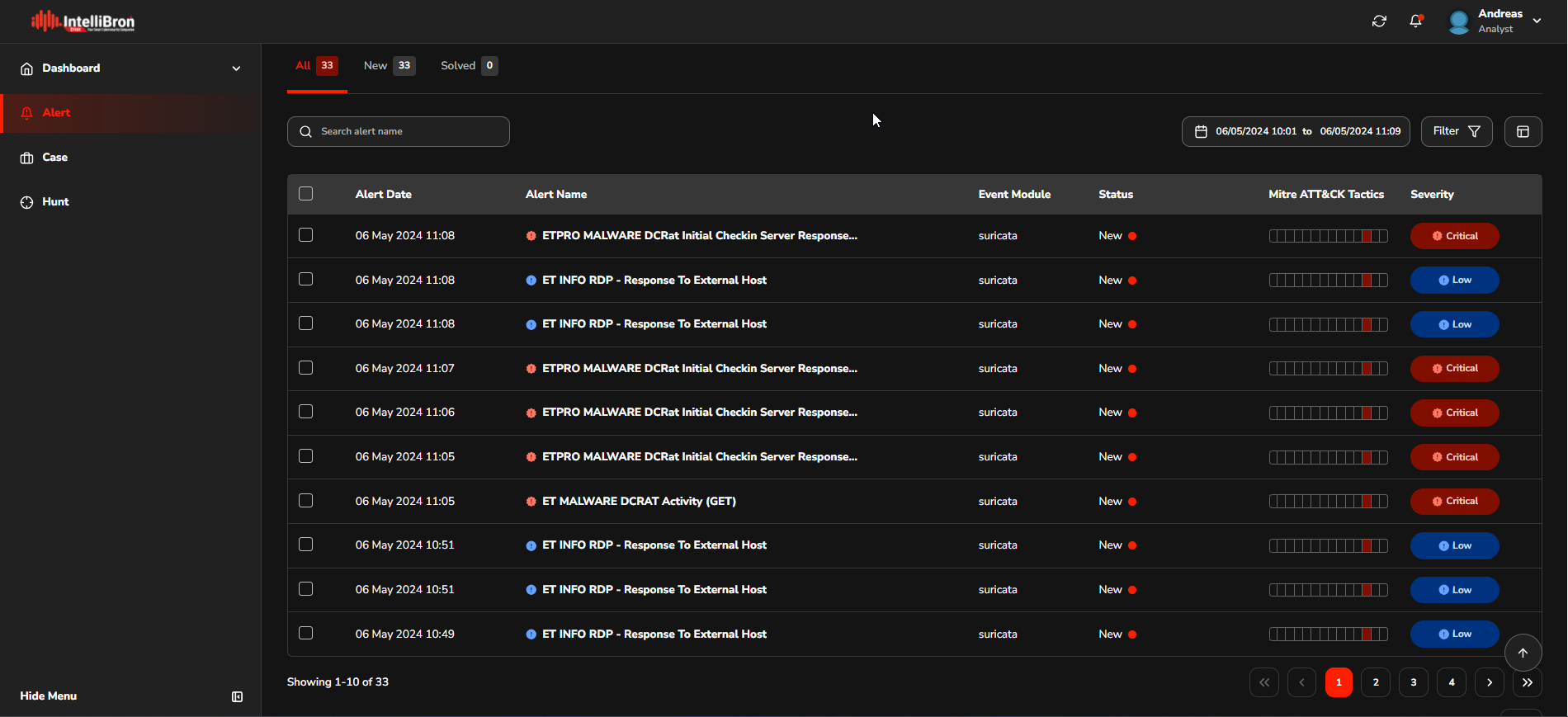
Upon execution of the malware, the IntelliBroń Orion generates an alert, which is then stored for later analysis. By reviewing these alerts using Bellatrix, the analyst can gain insight into the behaviour, impact, and potential security breaches caused by the malware.
To illustrate, let's consider one alert.
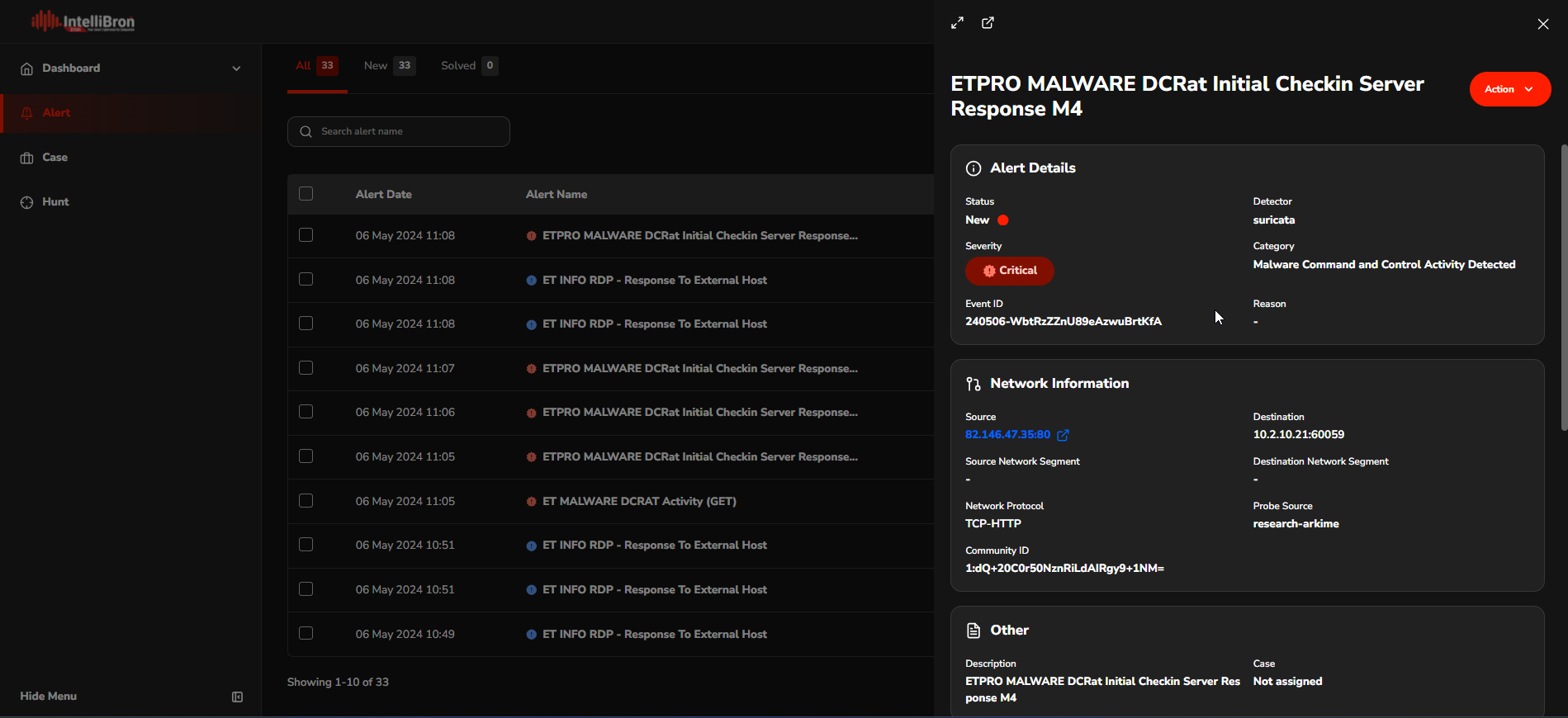
Each alert includes a feature that allows you to open the alert details on a single page, providing more detailed visibility related to the alert.
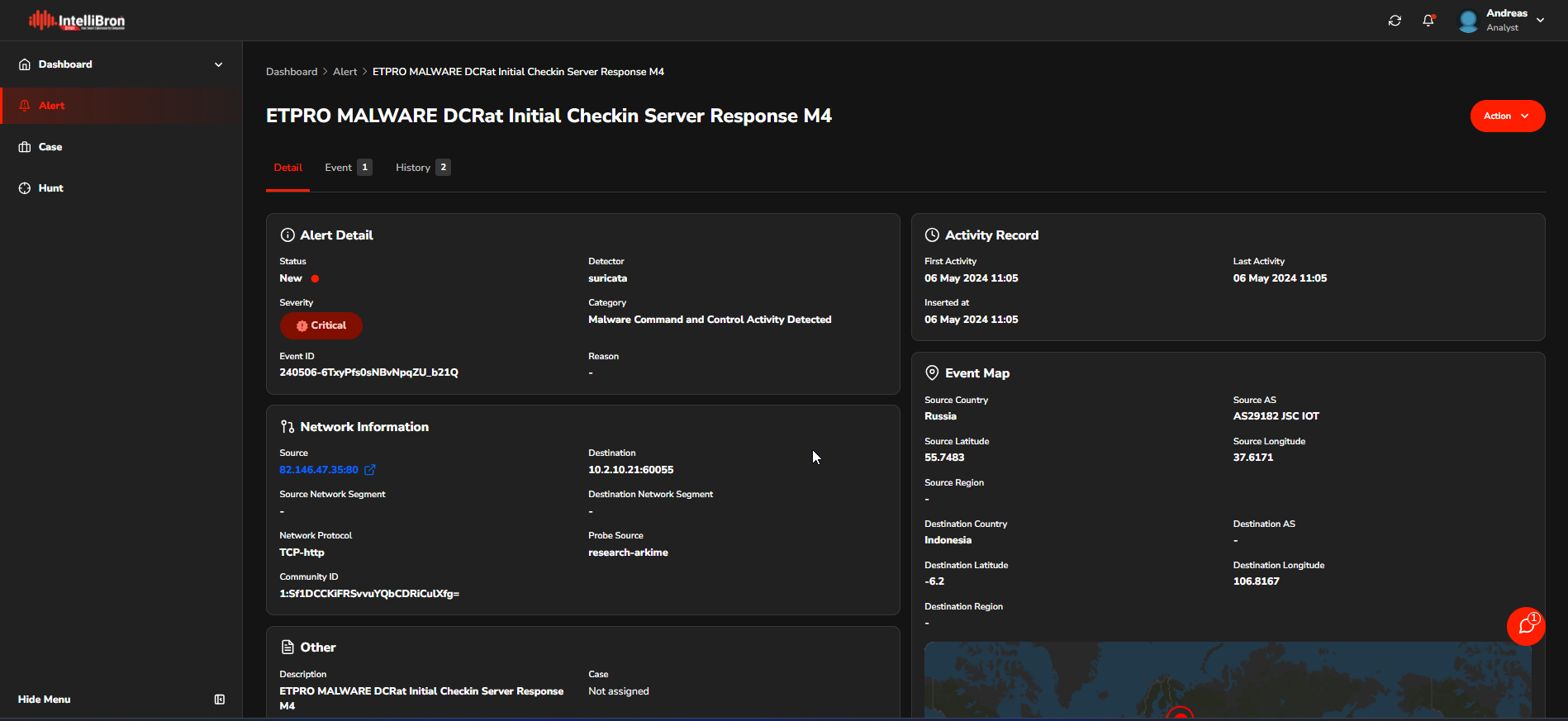
On the Detail page, the analyst can access additional information related to the alert.
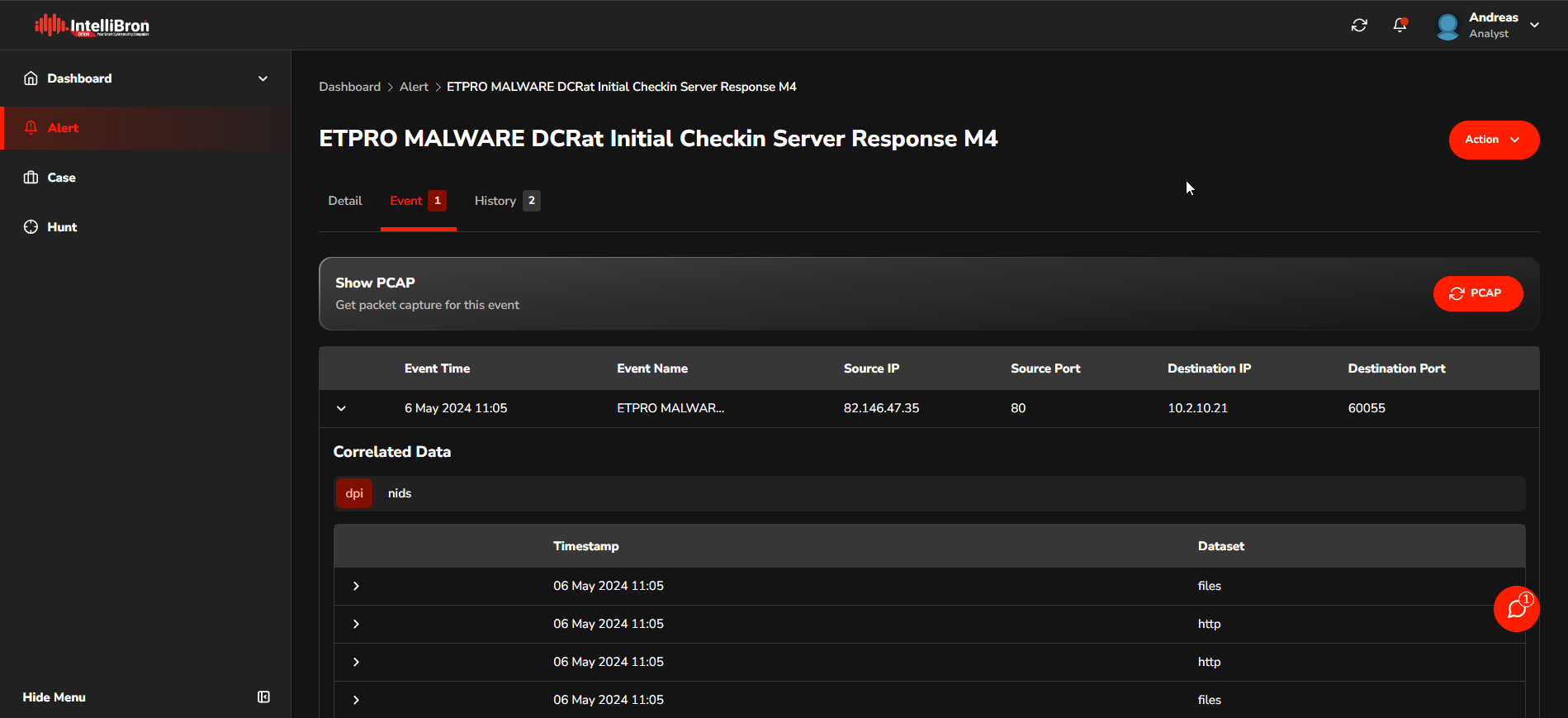
On the Event page, the Analyst can access detailed information about the alert by inspecting the aggregated data from the DPI (Deep Packet Inspection) and NIDS (Network Intrusion Detection System) sources.
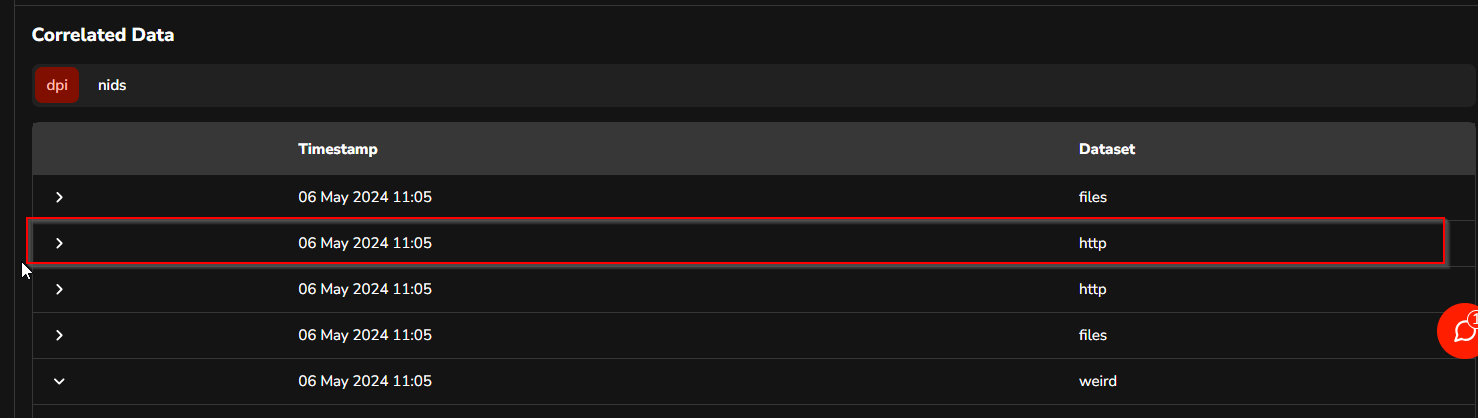
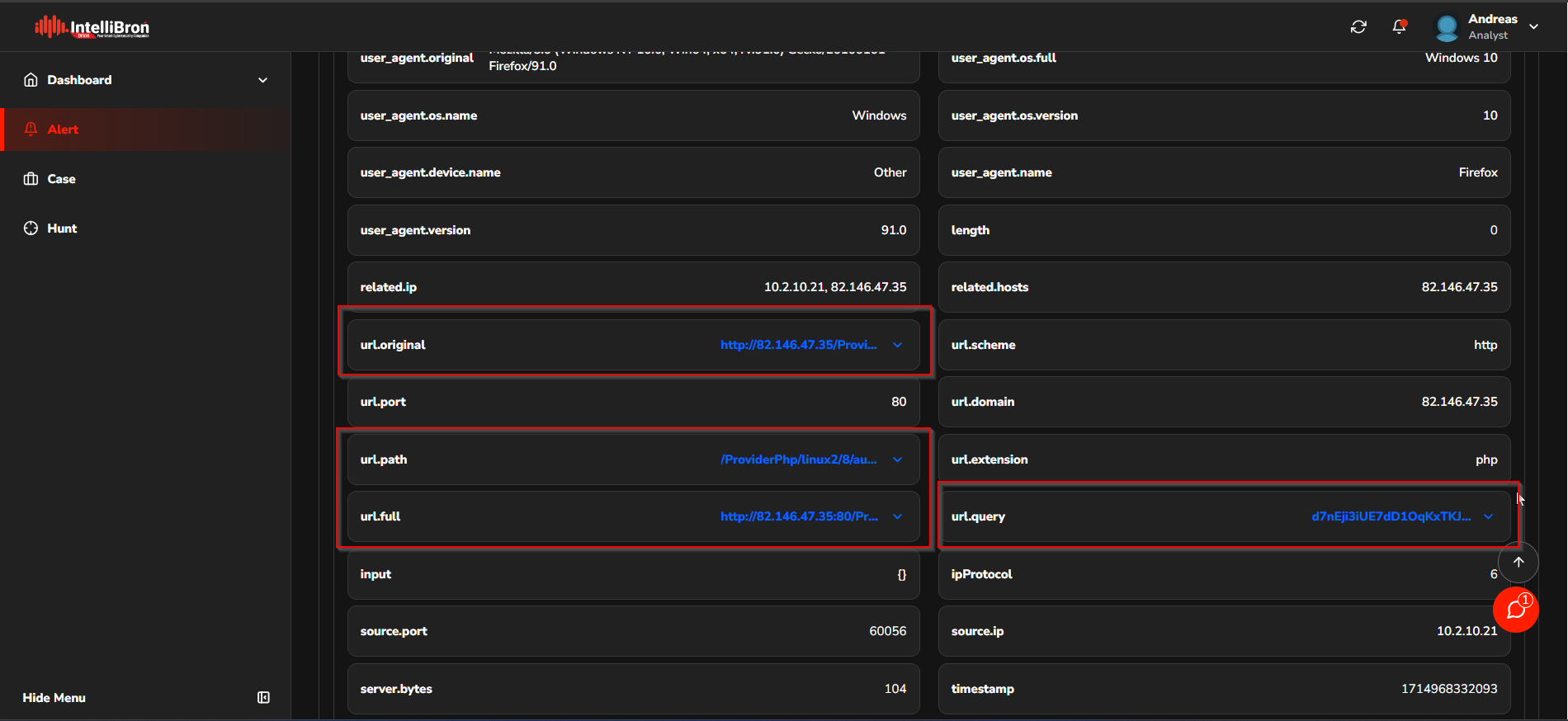
The Analyst can access more detailed information about alerts using the DPI > http dataset. This section allows the Analyst to view information related to URLs that have been accessed by the malware.
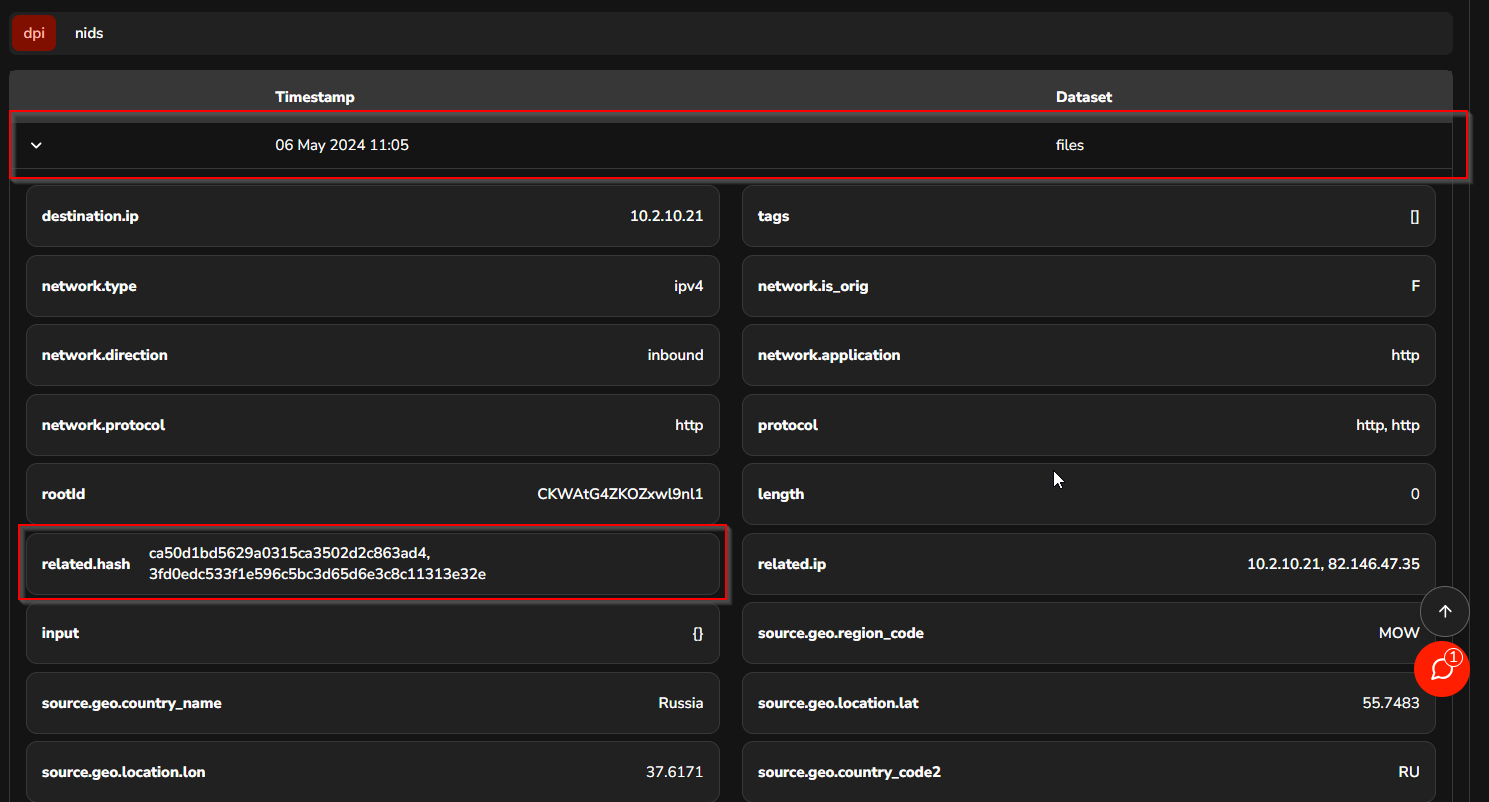
The analyst can inspect the files that have been downloaded using the DPI > Files dataset. This dataset contains information about the files to be analysed at a later stage.
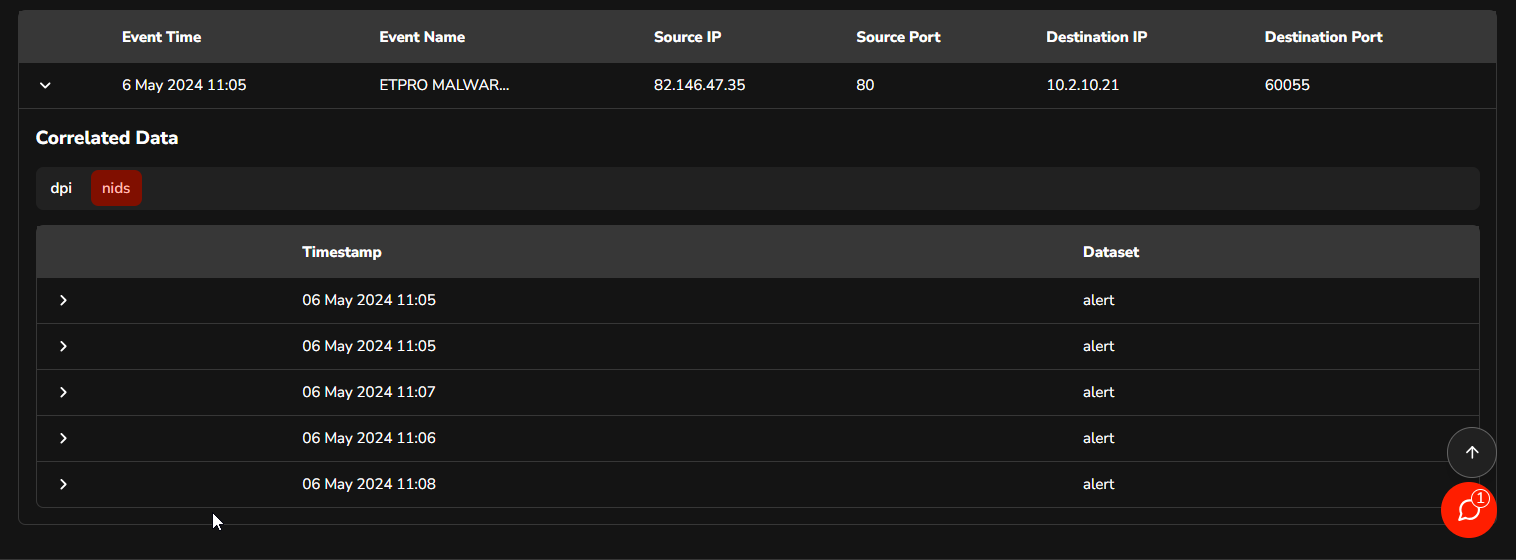
The NIDS > Alert dataset enables analysts to examine additional alerts related to the primary alert in question.
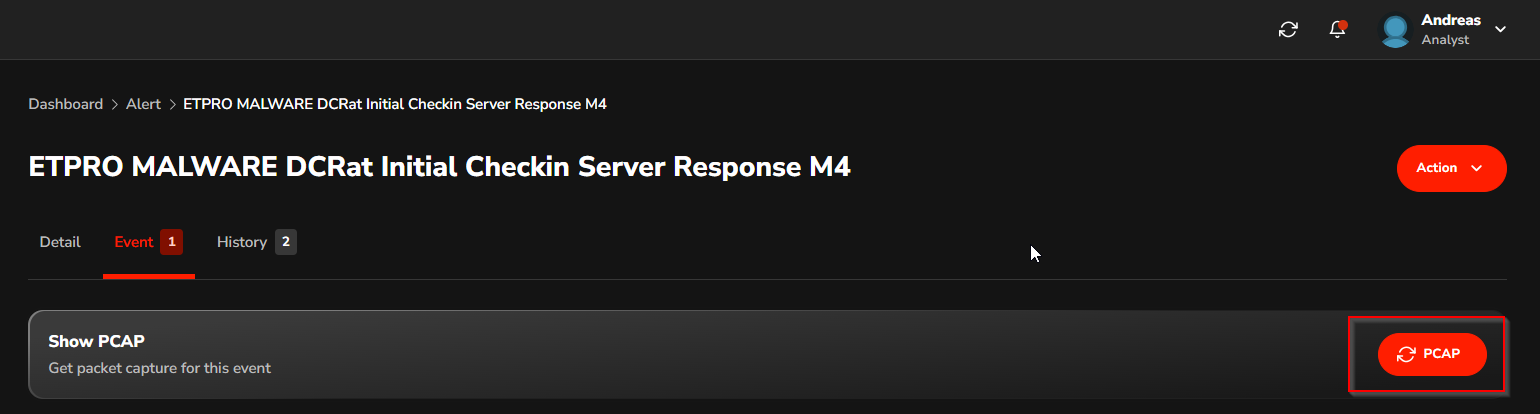
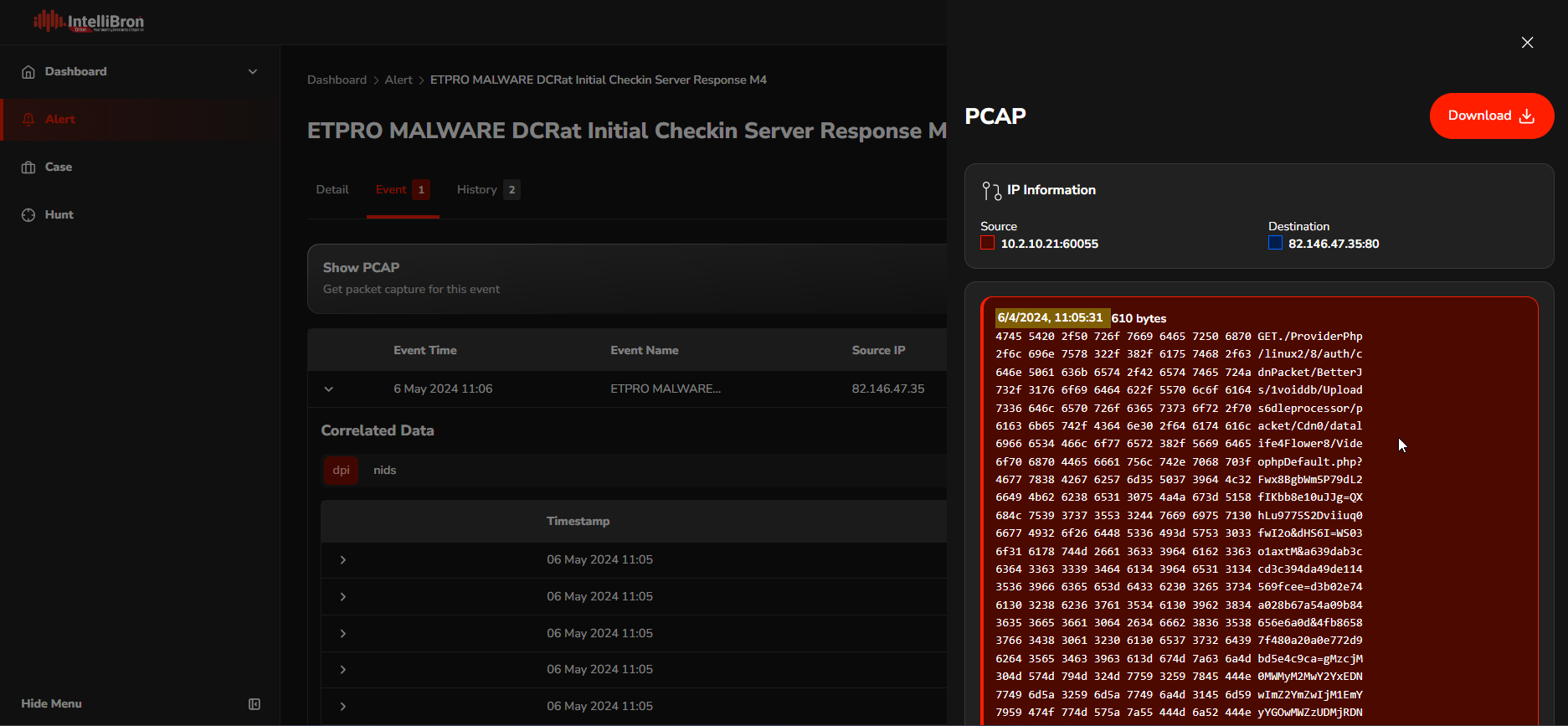
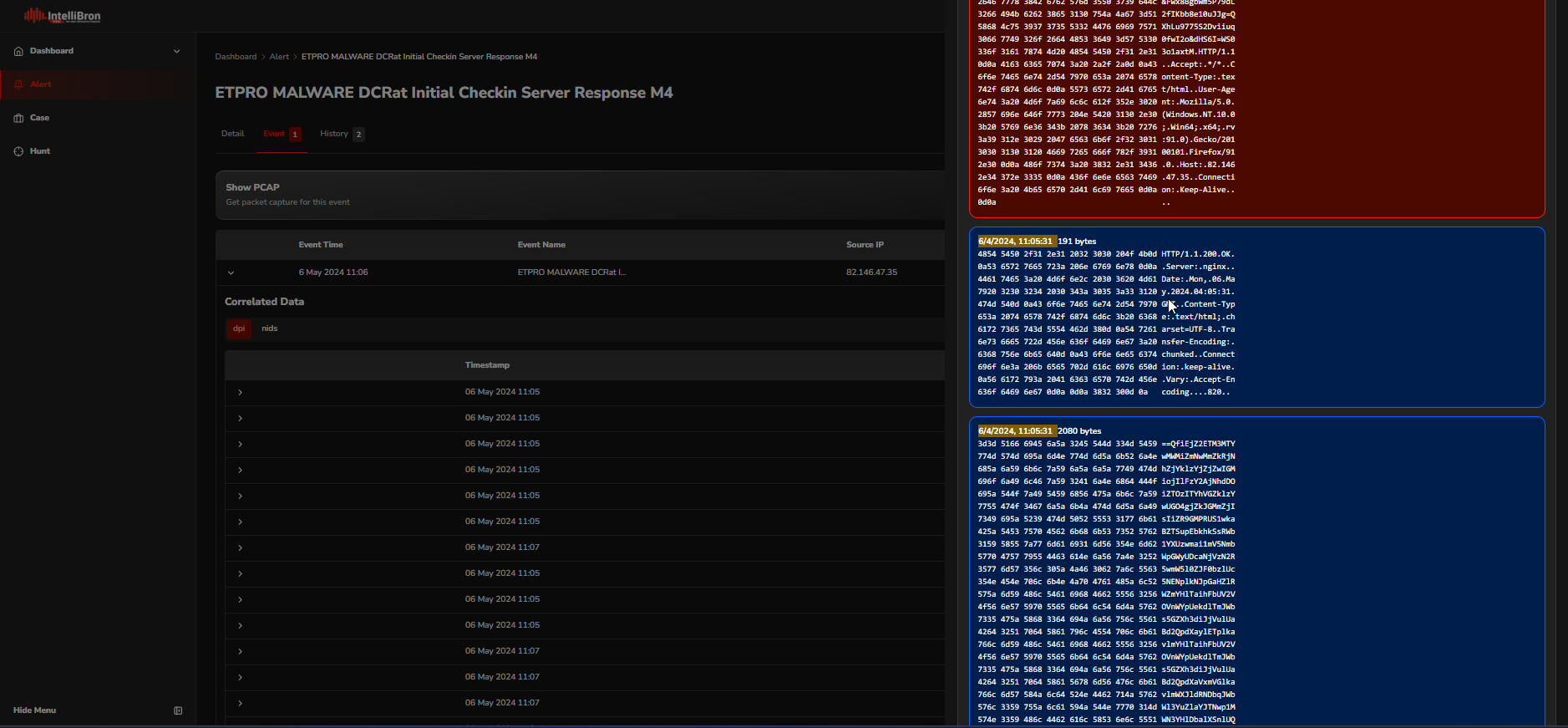
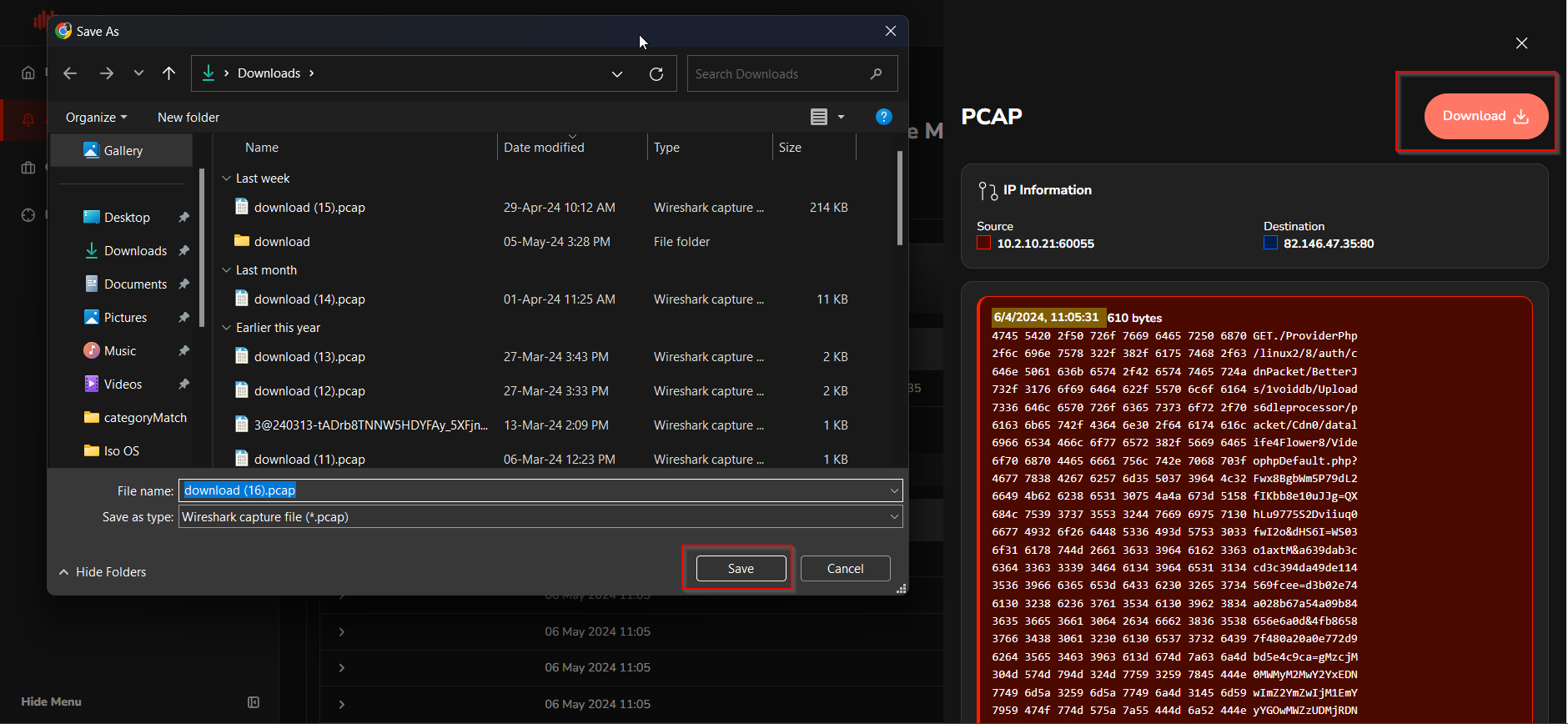
The analyst can download the PCAP file for a more detailed analysis using Wireshark. This process allows for the examination of network traffic in greater depth, enabling the analyst to identify individual packets that may indicate malicious activity or anomalies. The red box represents a request, and the blue box represents a response.
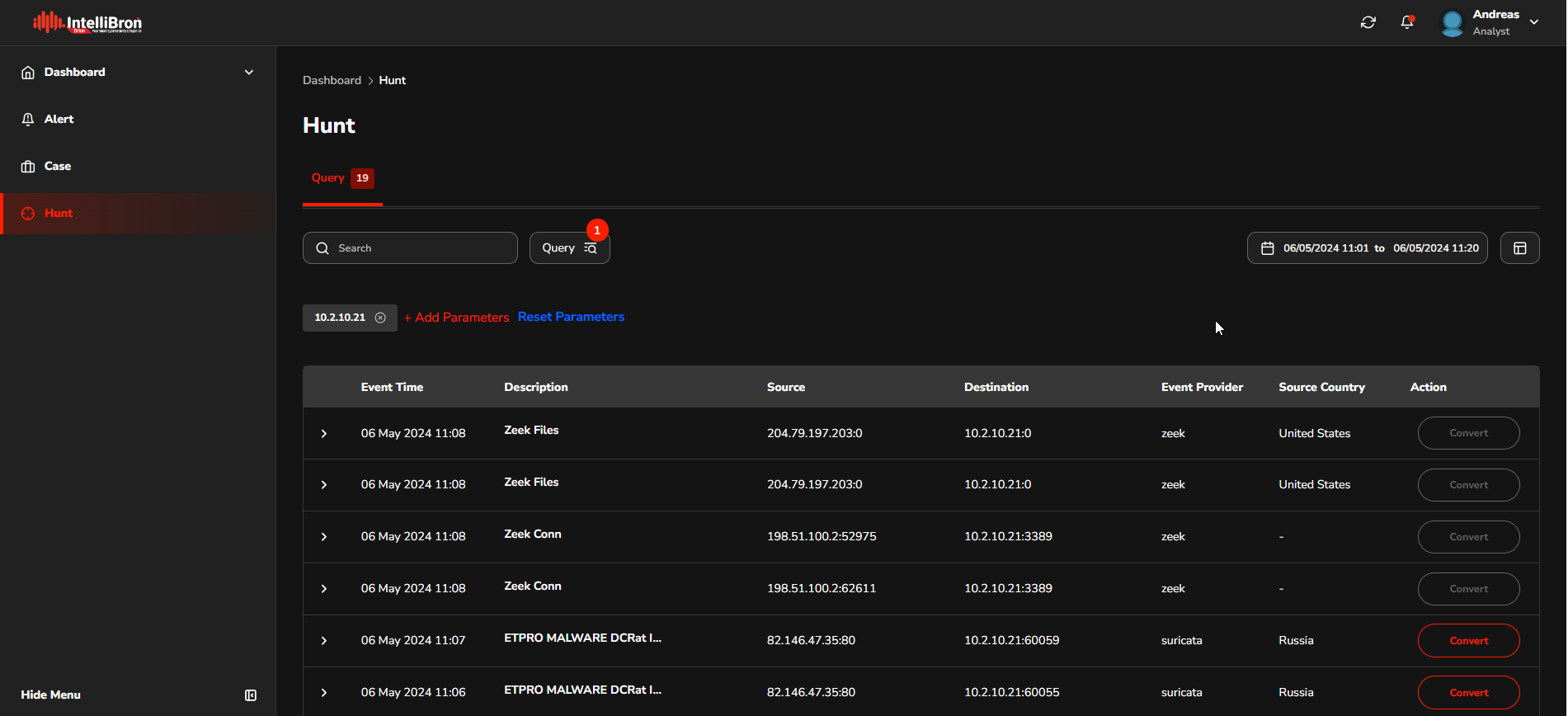
The "feature hunt" enables analysts to perform threat hunting on a specific timeline following the execution of malware. This allows them to identify Indicators of Compromise (IoCs) associated with the malware.
The feature enables analysts to systematically search through network and system data to pinpoint suspicious activities or artifacts that indicate a security breach. By focusing on the timeline after the malware has been executed, analysts can more effectively trace the actions of the malware, understand its impact, and gather crucial information about its behaviour. This is crucial for both neutralising the current threat and strengthening defences against future attacks.
Read more about our IntelliBroń Orion from its official website.






