Introduction
Organizations must be proactive in their defense against cyber attacks as they evolve and become more sophisticated. Threat intelligence is one way to improve cybersecurity. CrowdStrike defines threat intelligence as data that's collected, processed and analyzed in order to understand the motives of a threat actor, their targets and attack behavior. FireEye defines Cyber Threat Intelligence as knowledge based on evidence about adversaries, their intentions, capabilities, enabling environment and operations. It is focused on a specific event, series events, or trends and provides a decision advantage to the defense.
Threat intelligence gives organizations valuable insight into cyber threats. It identifies system and application weaknesses, allows them to proactively detect and respond to attacks and improves their overall cybersecurity posture. By leveraging a variety of sources of threat information, organizations are able to gain a better understanding of the current threat landscape and can take proactive measures to defend against possible attacks.
Threat Intelligence Sources
Threat intelligence sources are the various channels and means by which data is collected, analyzed, and processed to gain an understanding of potential cyber threats. These sources are classified as tactical, operational and strategic threat intelligence.
Tactical threat information is based on real-time data such as indicators for compromise (IOCs) that can be used by organizations to detect and respond effectively to active threats. Operational threat information focuses on patterns and trends in threat activity. This can help organisations develop more effective security policies. Strategic threat intelligence gives a broad view of the threat environment, including emerging threats and future risks. This can help organizations prioritize and plan their security initiatives.
Threat intelligence sources can be classified as either internal or external. Sources that are internal to the organization include security logs and employee reports. External sources are those that come from outside of the organization, such as social media feeds and dark web forums.
Organizations can make informed decisions on how to defend themselves against potential attacks by leveraging multiple sources of threat information. External sources provide a broad perspective on the threat landscape, whereas internal sources provide unique insight into a company's vulnerabilities and risks. Combining internal and external sources for threat intelligence allows organizations to develop security strategies tailored to their needs and risks.
We will look at examples of sources of threat information in the sections that follow. These examples will help you understand how to use each source to collect, analyze, and process threat intelligence data.
abuse.ch
abuse.ch provides threat intelligence based on community contributions. It hosts several projects to help Internet service providers and network operators secure their infrastructure against malware. Abuse.ch runs several platforms which provide valuable resources to the cybersecurity community. These platforms include:
Malware Bazaar
Platform where malware samples can be collected and shared to analyze. This platform allows you to share malware samples, as well as metadata like file names, sizes and hashes. The repository is regularly updated, and new samples are added daily.
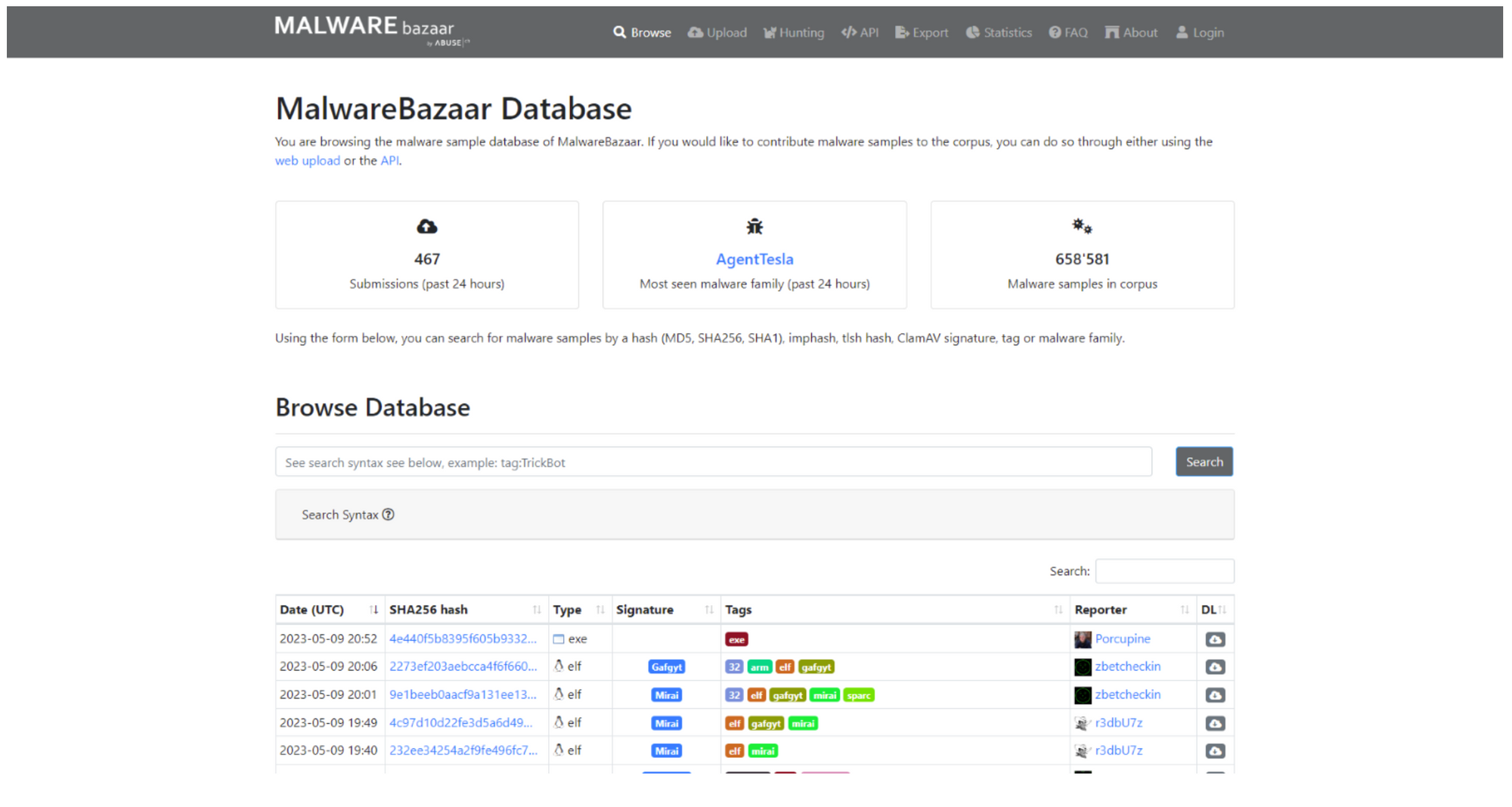
MalwareBazaar offers a variety of features that are useful for researchers and analysts. These include the ability to search specific samples and file hashes and to filter samples using keywords such as file type and signature.
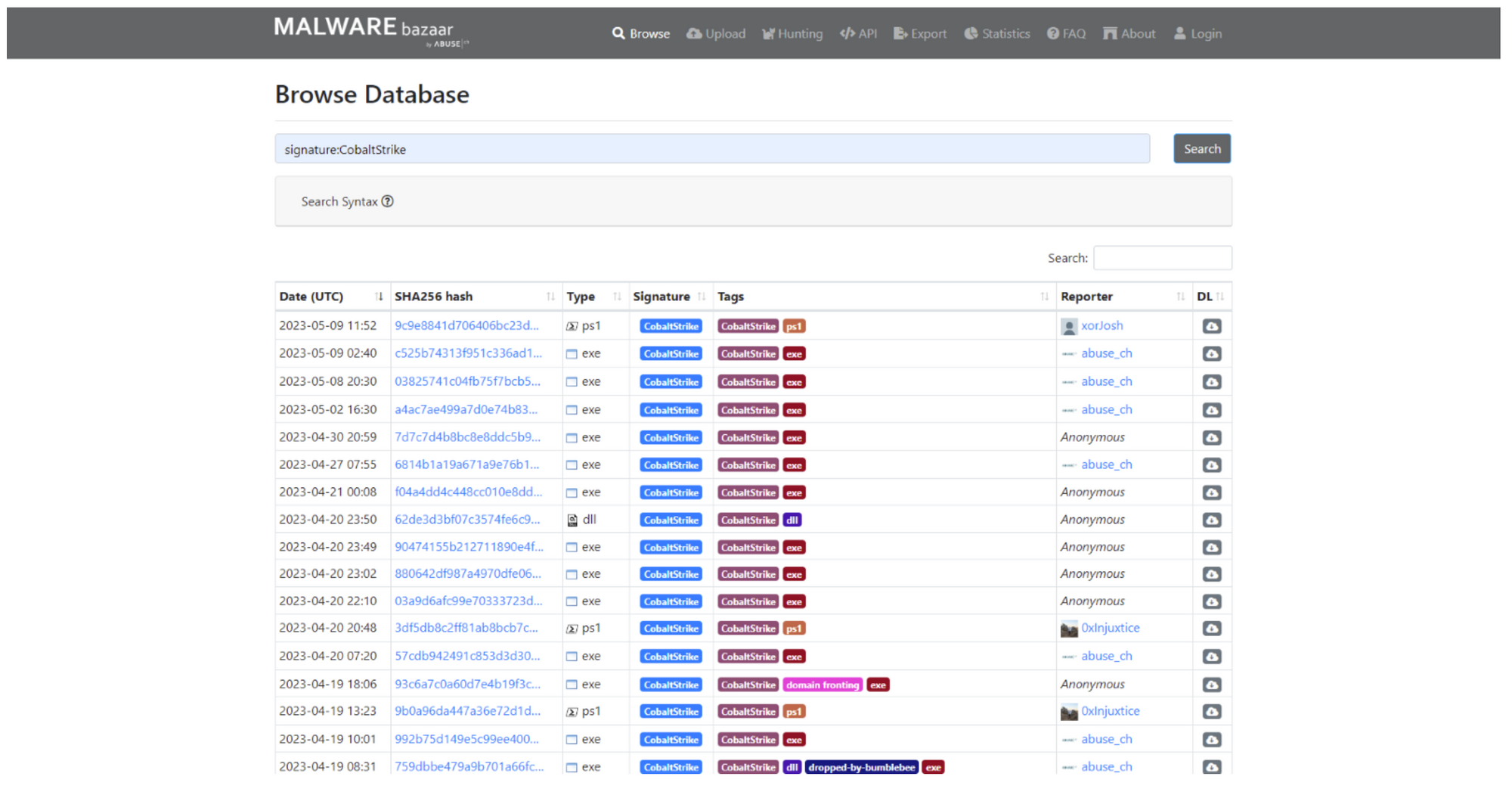
Users can also upload malware samples and query them using the platform API.
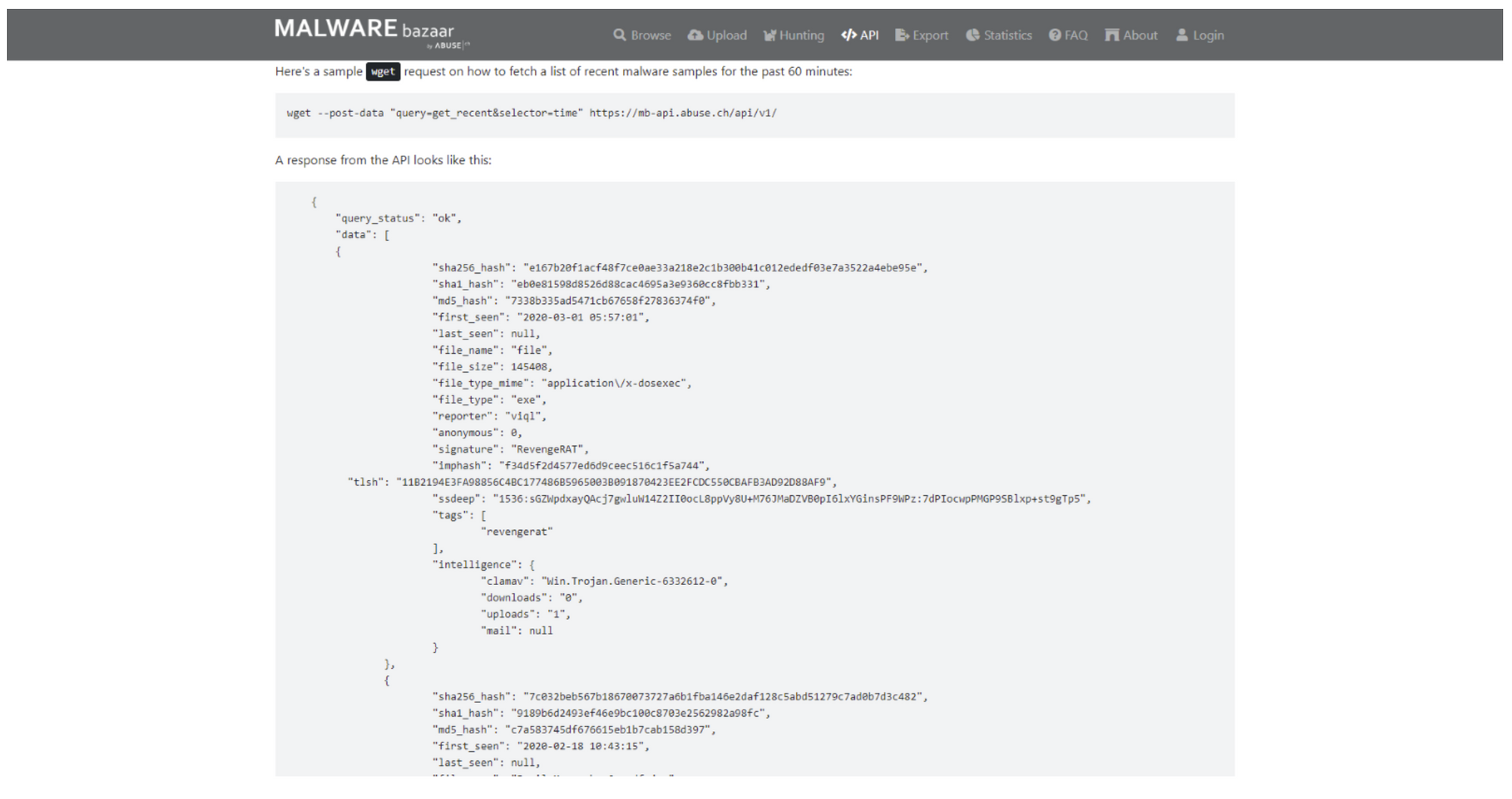
MalwareBazaar allows users to export their hash lists as CSV files, MISP daily events or other security tools.
Feodo Tracker
A platform that helps track botnet command and control infrastructure associated with Emotet, Dridex, and TrickBot.
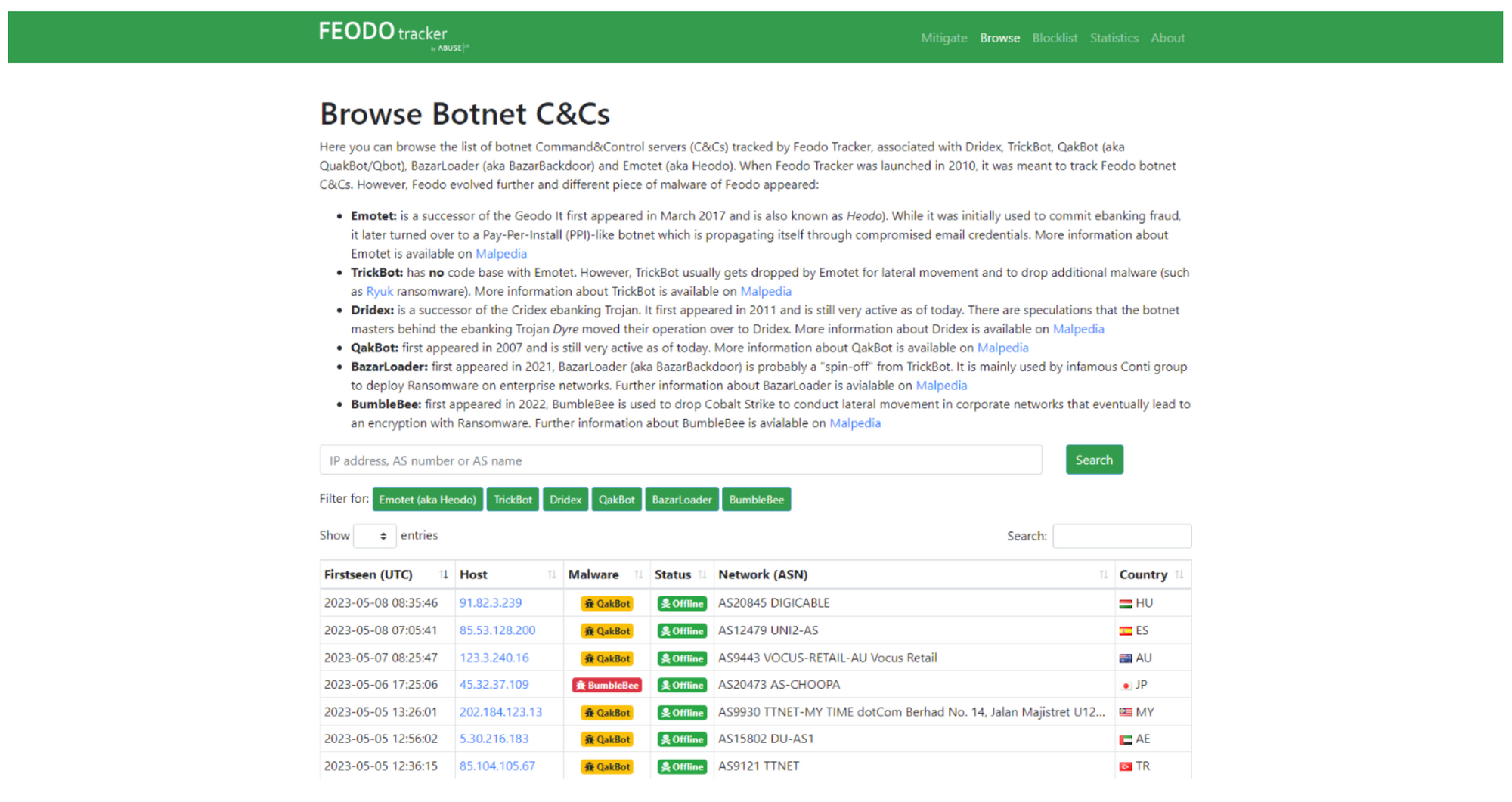
Feodo Tracker provides blocklists for various purposes in a variety of formats. They include:
- Botnet C2 Blocklist: List of IP addresses associated with botnet C2 Traffic. This list can help block traffic from C2 servers that are known and stop communication between infected machines and the botnet
################################################################
# abuse.ch Feodo Tracker Botnet C2 IP Blocklist (recommended) #
# Last updated: 2023-05-21 01:19:14 UTC #
# #
# Terms Of Use: https://feodotracker.abuse.ch/blocklist/ #
# For questions please contact feodotracker [at] abuse.ch #
################################################################
#
# DstIP
100.6.31.96
103.109.247.10
103.123.223.171
103.233.103.85
104.248.155.133
104.248.178.90
104.35.24.154
113.11.92.30
12.172.173.82
128.199.232.159
129.232.146.250
131.191.58.183
14.192.241.76
142.189.121.178
144.202.15.58
144.91.122.94
...- Botnet C2 indicators of compromise (IOCs), a list of domains and IP addresses as well as SSL certificates which have been identified to be part of botnet C2 in the last 30 days, or for all time.This data can be integrated into SIEM products to improve threat detection and alerts on potential botnet C2 traffic.Data is available in CSV, JSON and other formats
{
"ip_address": "178.128.23.9",
"port": 4125,
"status": "online",
"hostname": null,
"as_number": 14061,
"as_name": "DIGITALOCEAN-ASN",
"country": "SG",
"first_seen": "2021-05-16 19:49:33",
"last_online": "2023-05-21",
"malware": "Dridex"
},
{
"ip_address": "104.248.178.90",
"port": 4664,
"status": "online",
"hostname": null,
"as_number": 14061,
"as_name": "DIGITALOCEAN-ASN",
"country": "US",
"first_seen": "2021-07-28 16:01:42",
"last_online": "2023-05-21",
"malware": "Dridex"
},
{
"ip_address": "204.174.223.210",
"port": 9043,
"status": "offline",
"hostname": "lsh414.van.ca.siteprotect.com",
"as_number": 14280,
"as_name": "NETNATION",
"country": "CA",
"first_seen": "2021-08-14 18:40:26",
"last_online": "2023-04-25",
"malware": "Dridex"
},
...- Suricata botnet C2 IP ruleset: Set of rules that can be applied to the Suricata intrusion prevention and detection system in order to block botnet C2 traffic using IP addresses
SSL Blacklist
A platform which collects and provides a list of malicious SSL certificates, JA3/JA3s fingerprints, and botnet C&C servers
SSL Blacklist provides a variety of blacklists that can be used in various formats.The Suricata SSL Certificate Ruleset, a ruleset that is used with the Suricata IPS/IDS, blocks SSL certificates for known malicious domains.The Botnet C2 IP Blacklist is a blacklist of IP addresses associated with botnet C&C server. The Suricata Botnet C2 IP ruleset is a ruleet which blocks traffic from known Botnet C&C Servers.
SSL Blacklist offers a Botnet C2 IPDNS Response Policy Zone (RPZ) that can be used to prevent DNS requests from known botnet C&C server.The JA3 Fingerprint Blacklist is a blacklist of JA3 Fingerprints. The Suricata JA3 Fingerprint Ruleset blocks traffic from malware botnets based upon their JA3 Fingerprints.
URL Haus
Platform where information about malware sites is shared.Users can submit new URLs to be included in the database, and use the URLhaus API for downloading the database in CSV format.
URLhaus provides a variety of blacklists, in various formats and for different purposes.Daily MISP Events are a list of all URLs added to URLhaus in the last 24 hours.DNS Response Policy Zone is a DNS blocklist which can be used to prevent access to malicious domains. Snort/Suricata IDS Ruleset is a collection of rules that are used by the Snort/Suricata IDS/IPS to detect and block traffic from malicious domains. The hostfile is just a list of domains which can be used to prevent access to malicious domains.
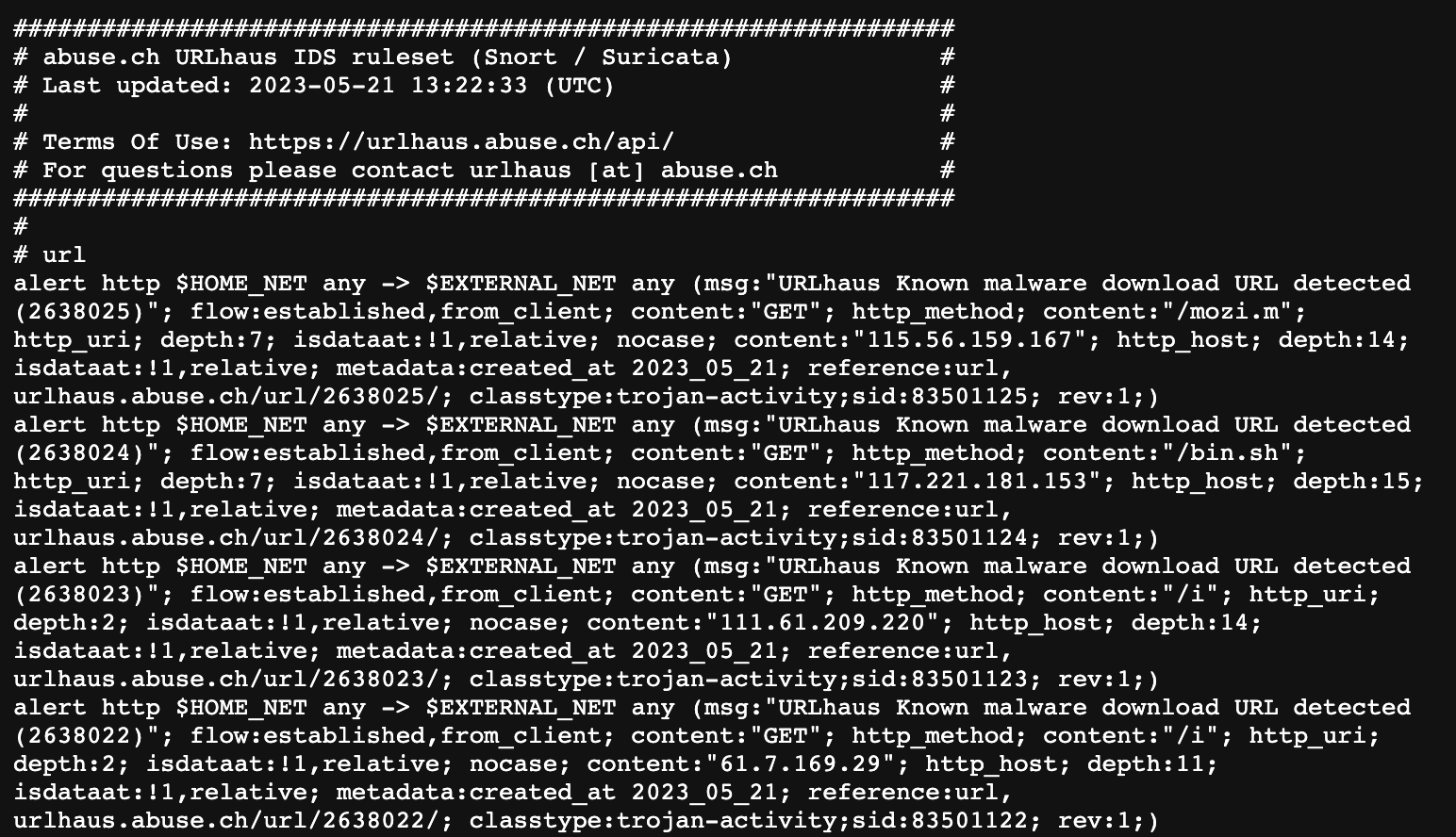
URLhaus also provides two other lists: a Plain Text URL List (URLs Only) which contains all URLs from the URLhaus database and a CSV list, which contains metadata for each payload collected by URLhaus.
ThreatFox
ThreatFox is a free platform from abuse.ch with the goal of sharing indicators of compromise (IOCs) associated with malware with the infosec community, AV vendors and threat intelligence providers.
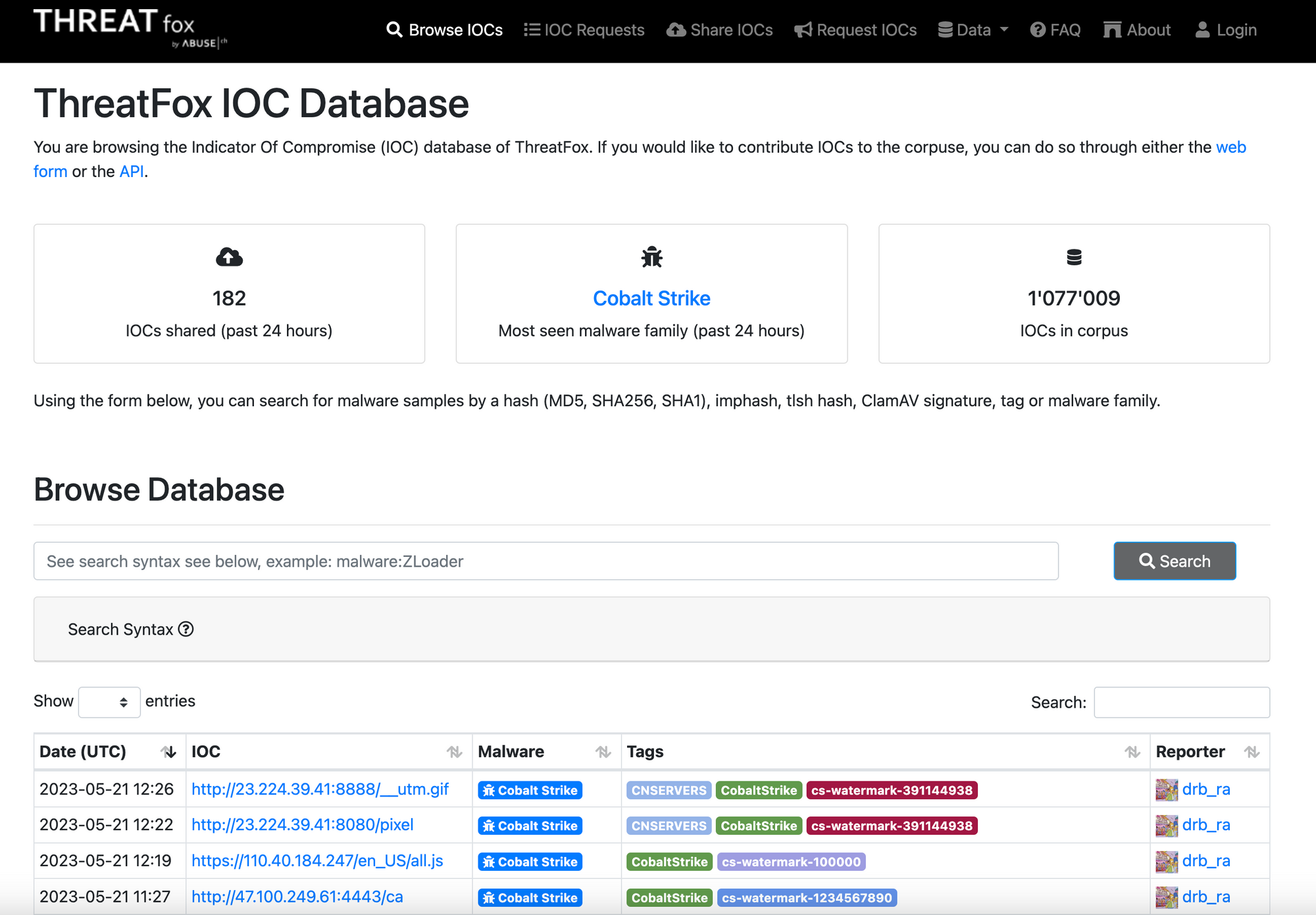
The platform allows users to contribute IOCs through either the web form or the API.ThreatFox also offers the exporting of IOCs in various formats, including daily MISP events, Suricata IDS rulesets, DNS Response Policy Zone (RPZ), host files with domains only, JSON files, and CSV files.By sharing IOCs, ThreatFox helps to improve the detection and prevention of malware attacks.
Yaraify
YARAify is a project from abuse.ch that allows anyone to scan suspicious files such as malware samples or process dumps against a large repository of YARA rules. With YARAhub, the platform also provides a structured way for sharing YARA rules with the community.
Users can set up custom alerts to hunt for newly observed files in YARAify, for example, for a specific YARA Rule, Imphash or ClamAV Signature.Users can receive new matches for the hunting rules via email or Pushover. This is available on mobile phones and web-browsers.
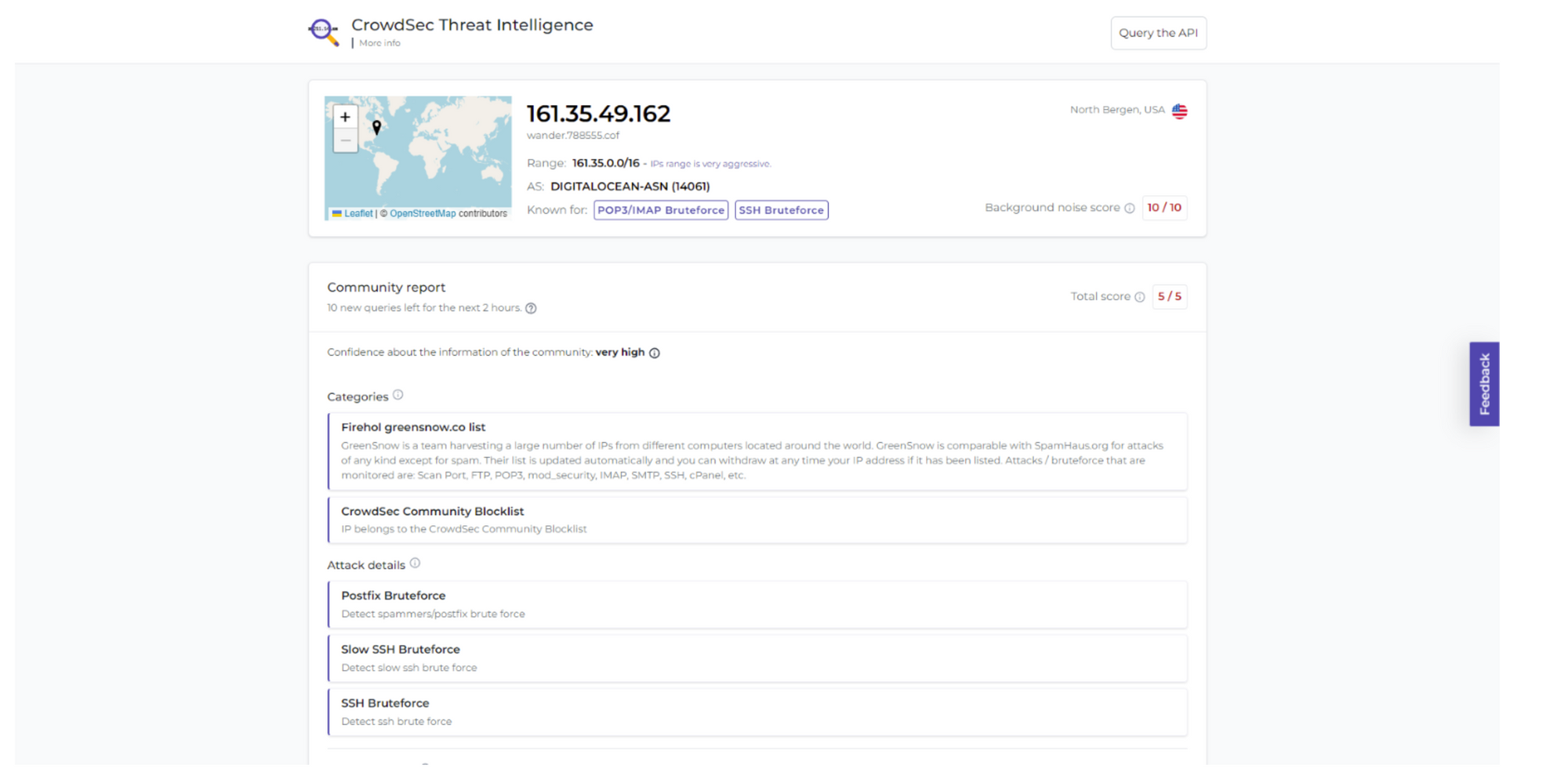
CrowdSec Threat Intelligence
CrowdSec threat intelligence is a source of security intelligence that collects millions of signals each month from tens and thousands of users.It is the largest source of threat intelligence in the world, and it has an advanced curation system that eliminates all false positives and poisoning attempts. This ensures users get the most accurate information possible.CrowdSec's Threat Intelligence API can be used to query the data and assess each flagged IP (Country, autonomous system level, type, and aggressiveness of attack).The CrowdSec feed can also be connected to a Threat intelligence platform to identify offensive IPs (i.e.The incoming traffic can be analyzed for Tor usage, proxy usage, and CVEdetection.
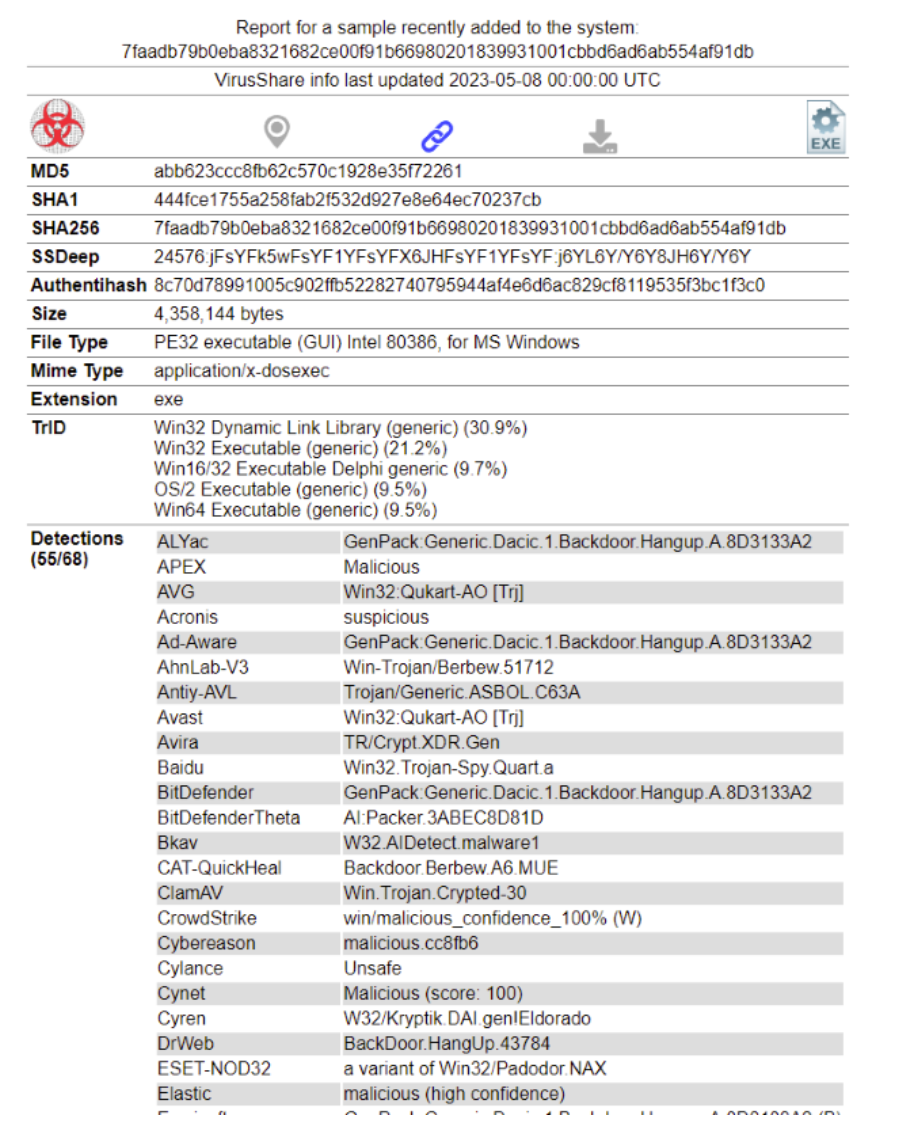
VirusShare
VirusShare.com provides a platform for accessing malware samples. This is useful for security researchers, incident response teams, forensic analysts and anyone else interested in malicious code. Access to the site is by invitation only, and requests can be sent via email to Melissa at Melissa97@virusshare.com with 'access' in the subject line. The use of bots, or any other method to scrape or download excessively samples is prohibited.
VirusShare does not accept responsibility for any damage or infection that may result from accessing this site. All samples are delivered as password-protected ZIP-files. The password for each sample is "infected". The platform can be followed via Mastodon at @VXShare@infosec.exchange and is maintained by Corvus Forensics.
OpenPhish
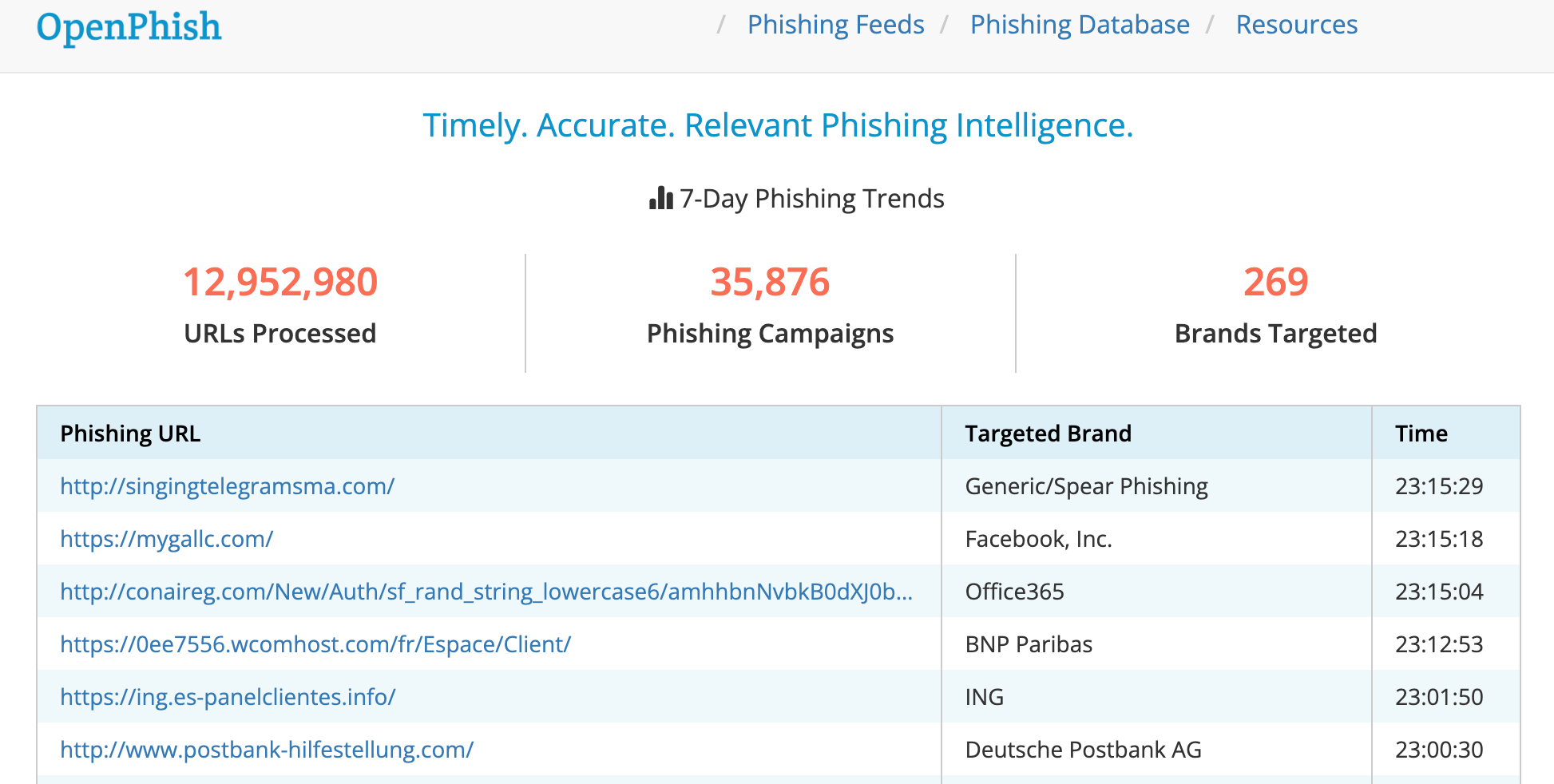
OpenPhish, a phishing platform for intelligence, helps companies detect and prevent phishing. It is an automated platform that performs real-time intelligence analysis without any human interaction and without relying on external resources such as blacklists.
OpenPhish provides actionable intelligence on active phishing attacks. The restricted community feed offers a list updated every 12 hour of phishing URLs. OpenPhish's premium feeds are updated every five minutes, and include additional data such as brand, industry and page.
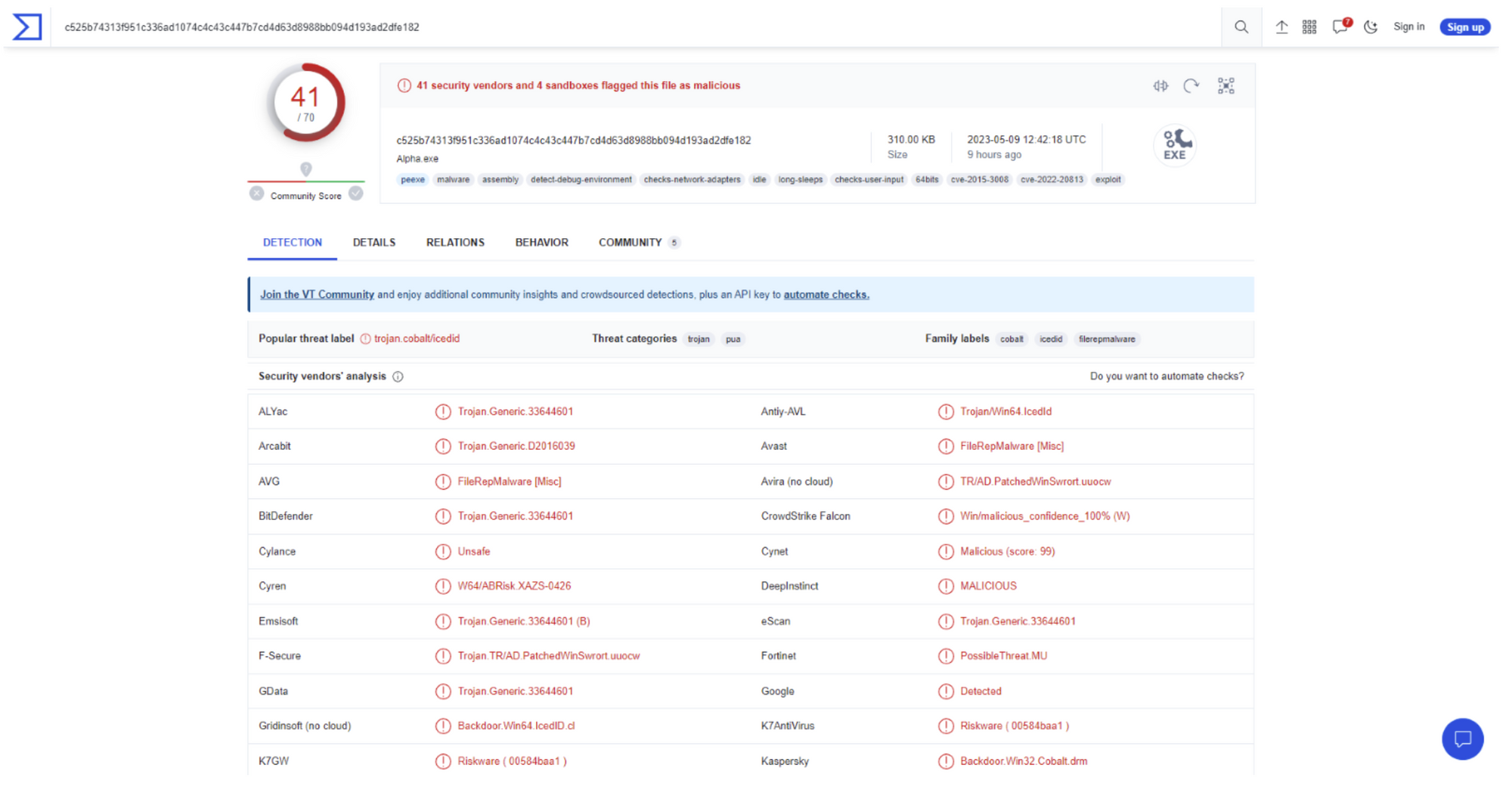
VirusTotal
VirusTotal offers a free online service for scanning URLs, viruses and malware. It uses over 70 antivirus scanners, URL/domain blocking services and a variety of tools to extract information from the content. Users can send VirusTotal any file they choose from their computer. VirusTotal provides a variety of ways to submit files, such as web interface uploads, APIs, or desktop and browser applications.
There is a premium service, VirusTotal intelligence, that offers additional features, such as customizable alerts and advanced search capabilities.
ThreatFeeds
Threatfeeds.io, a web platform, collects and curates threat intelligence feeds that come from a variety of sources. Threatfeeds offers open-source and freely accessible threat intelligence feeds. Some feeds require direct access to their source pages.
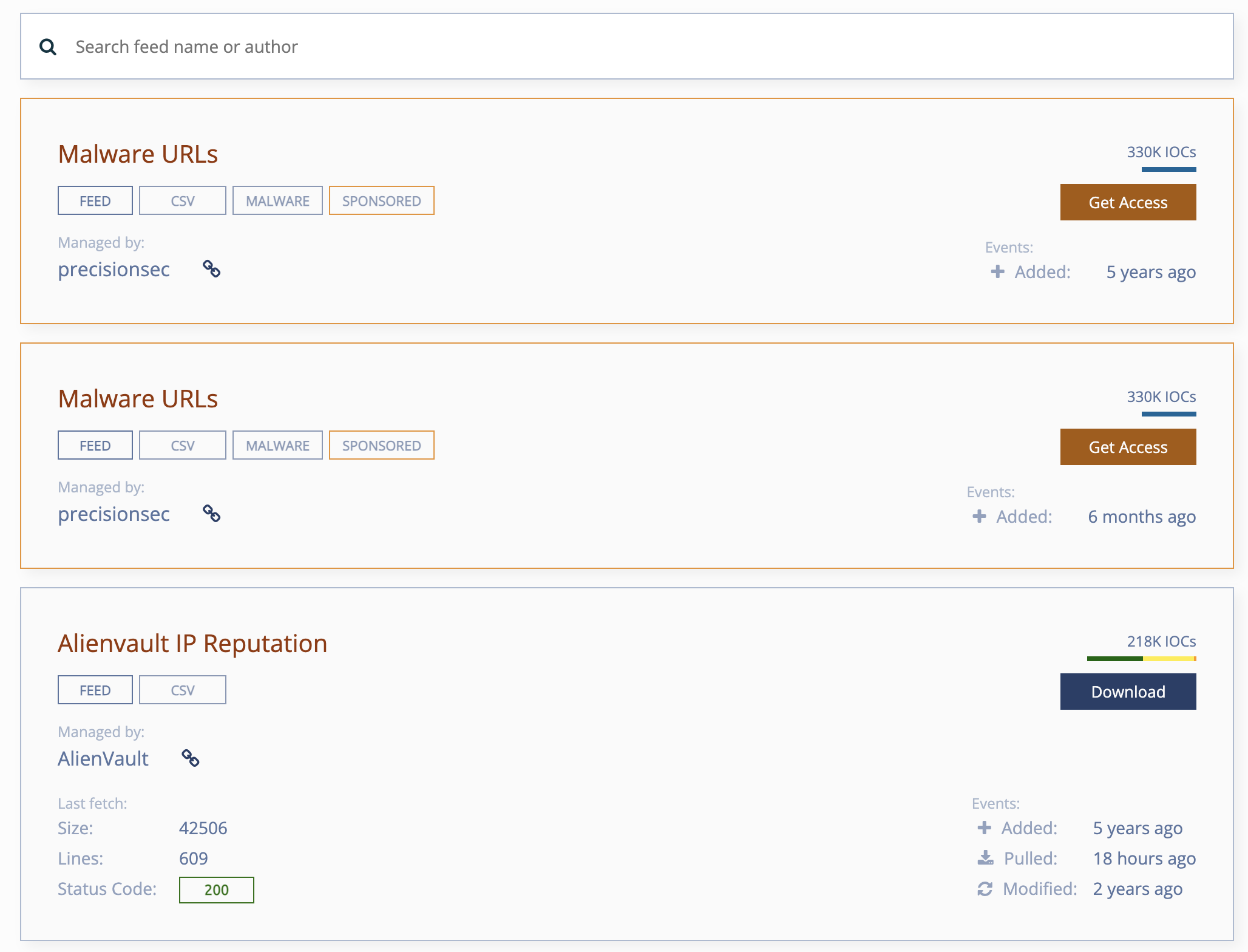
The accessibility of Threatfeeds, with its user-friendly interface and easy search function, is one of the main benefits. Users can browse and search feeds in order to quickly identify relevant information. This site offers feeds covering a variety of threats such as spam, malware, phishing and botnets.
Some feeds were not accessible at the time this article was written. However, ThreatFeeds is a great example of a framework that collects threat intelligence from different sources. We can use this to gather more private sources.
Threat Intelligence Platform
A Threat Intelligence Platform (TIP) is a software that allows organizations to gather, process and analyze threat intelligence from various sources. It provides a comprehensive picture of the threat landscape, by aggregating information from internal and external sources such as security logs and social media feeds.
TIPs enriches data with contextual information such as geolocation, threat intelligence specific to industry, and vulnerability assessments. This data is enriched to help identify new threats, investigate possible threats, and prioritize your security initiatives.
TIPs provide automation and collaboration features that allow security teams to collaborate more effectively. They can also automate repetitive tasks. These features include the ability to share threats, customize dashboards and workflows in response to incidents.
CrowdStrike Falcon Intelligence
CrowdStrike's Falcon Intelligence, an automated threat intelligence system that delivers a global IOC in real time, is a solution for automating the collection of threat information. By monitoring malicious activity on the deep, open and dark web, it allows organizations to protect their brand and employees as well as sensitive data.
CrowdStrike Falcon’s threat detection engine uses machine learning, malware behavior identifiers and threat intelligence in order to detect attacks, even those from new malware. The CrowdStrike Falcon platform allows users to visualize the relationships between IOCs, adversaries and endpoints. They can also hunt for threats using IOCs that are enriched with contextual information.
The following CrowdStrike's Falcon Intelligence screen shot shows the detection of a malicious gspider.exe file. The file is in "detection" phase, which means that it has been identified and blocked from running on the system. The threat's severity is "high," which means it poses a serious risk to the computer and possibly the entire organization. Falcon has quarantined the file, stopping it from doing further damage.
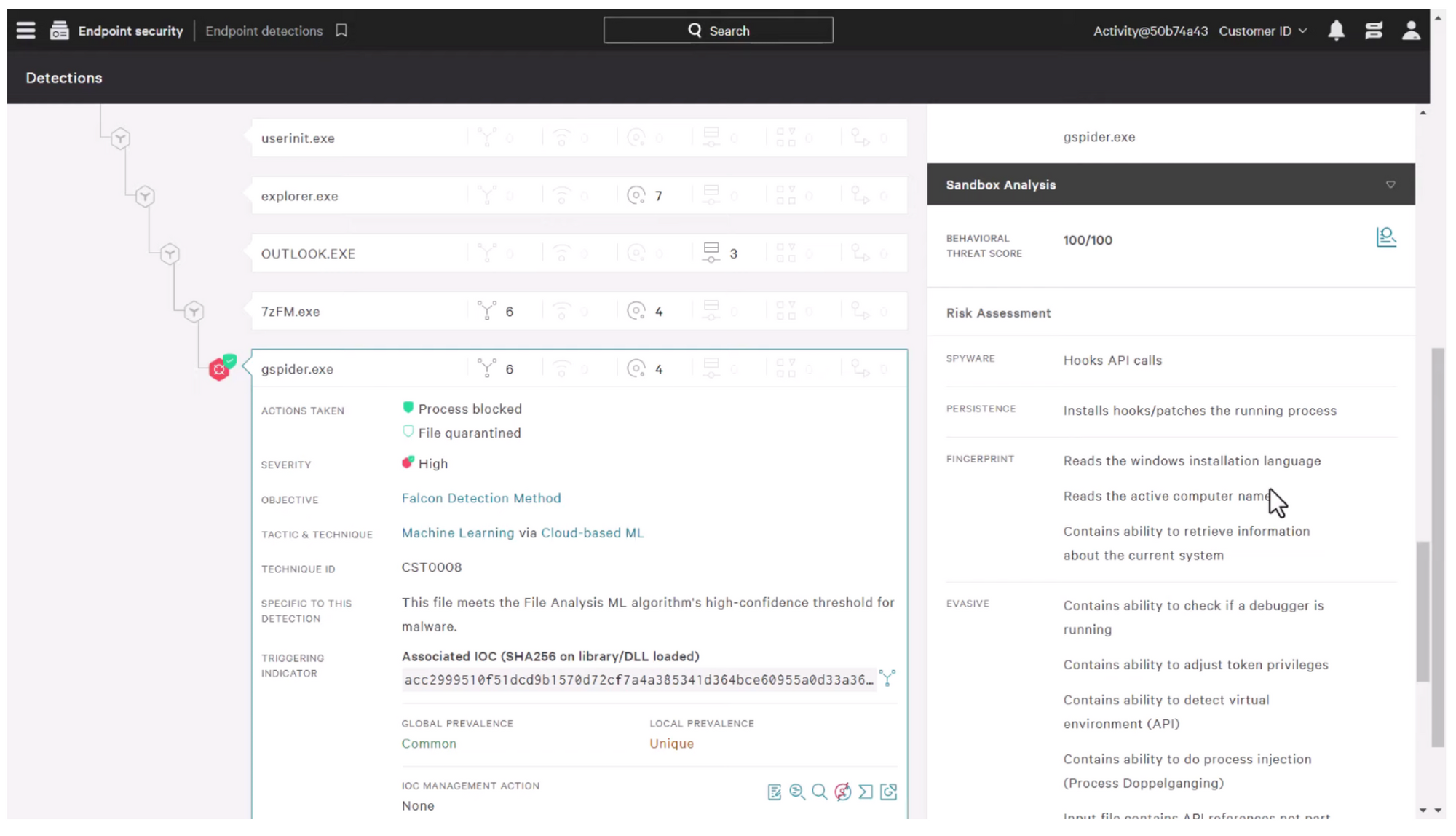
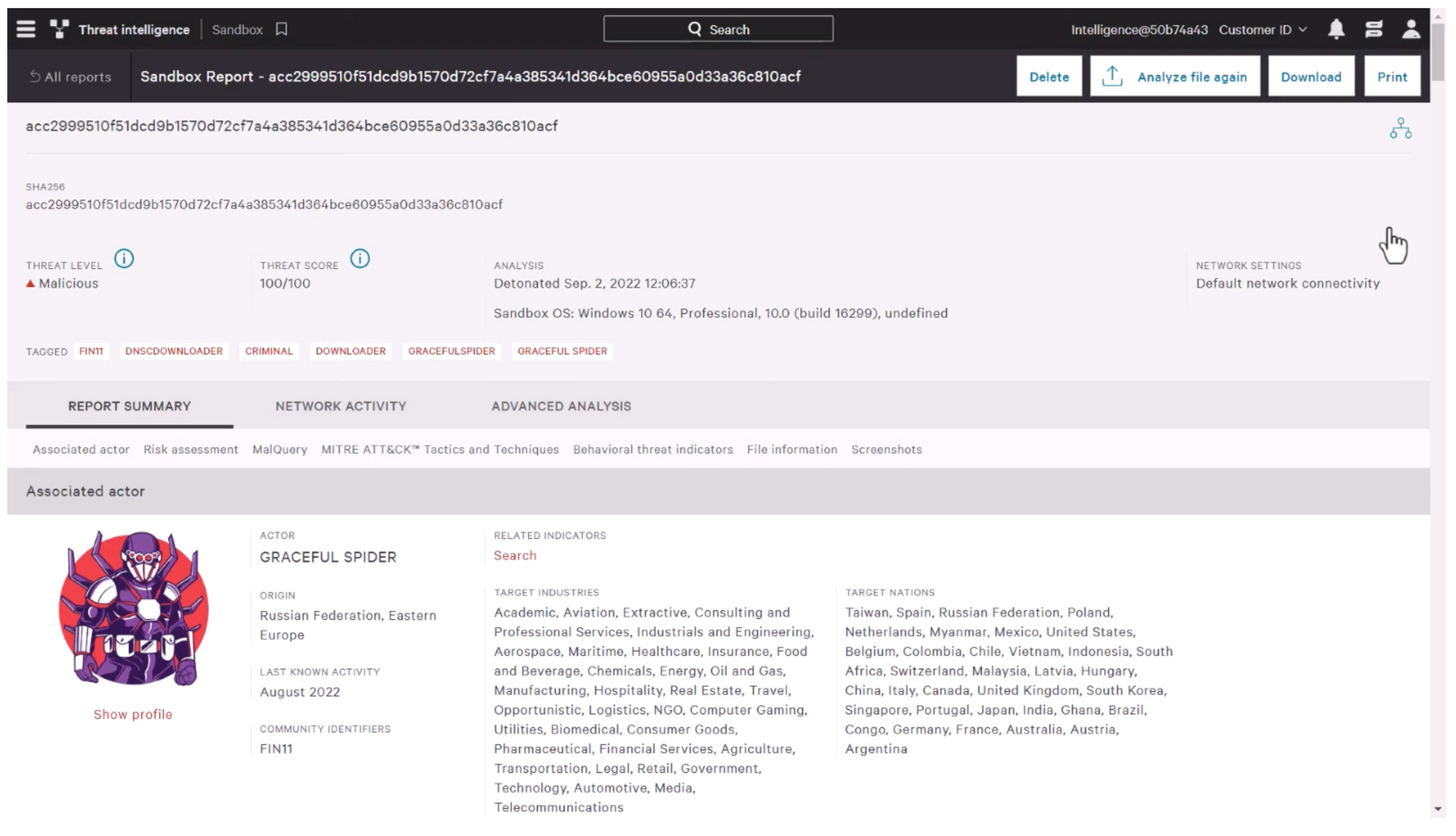
The following screenshot below shows the file being sent to a sandbox for analysis. The Falcon platform will evaluate the behavior of the file in this isolated environment and provide a behavioral threat assessment, risk assessment, as well as a MITRE AT&CK matrix mapping.
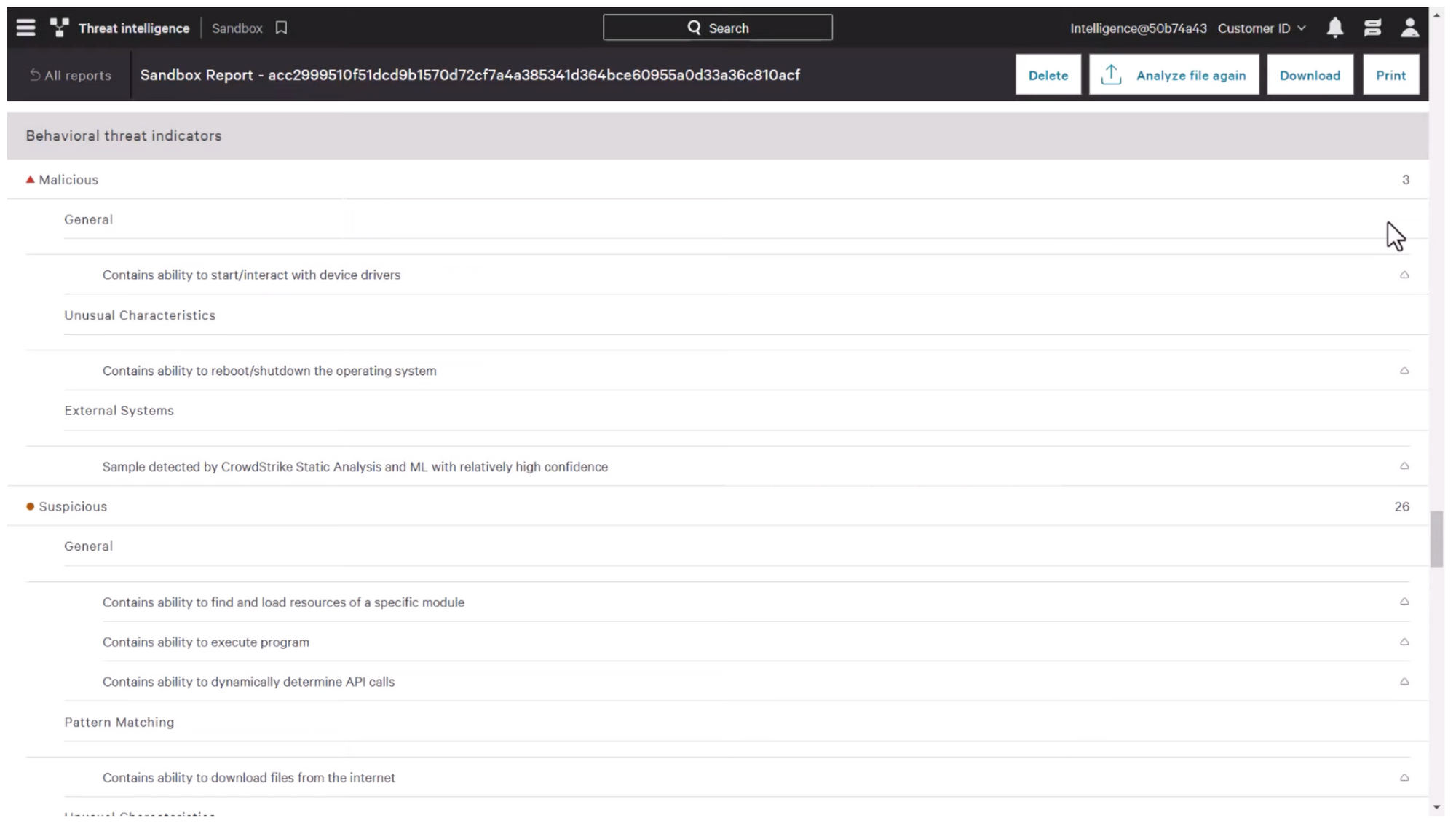
The analysis will give you a deeper understanding of the file's capabilities, and its potential impact on your system and organization. The behavioral threat scores indicate the degree of malicious behavior observed during the sandbox analyses, while the risk assessments provide an overview of the potential impact of the file.
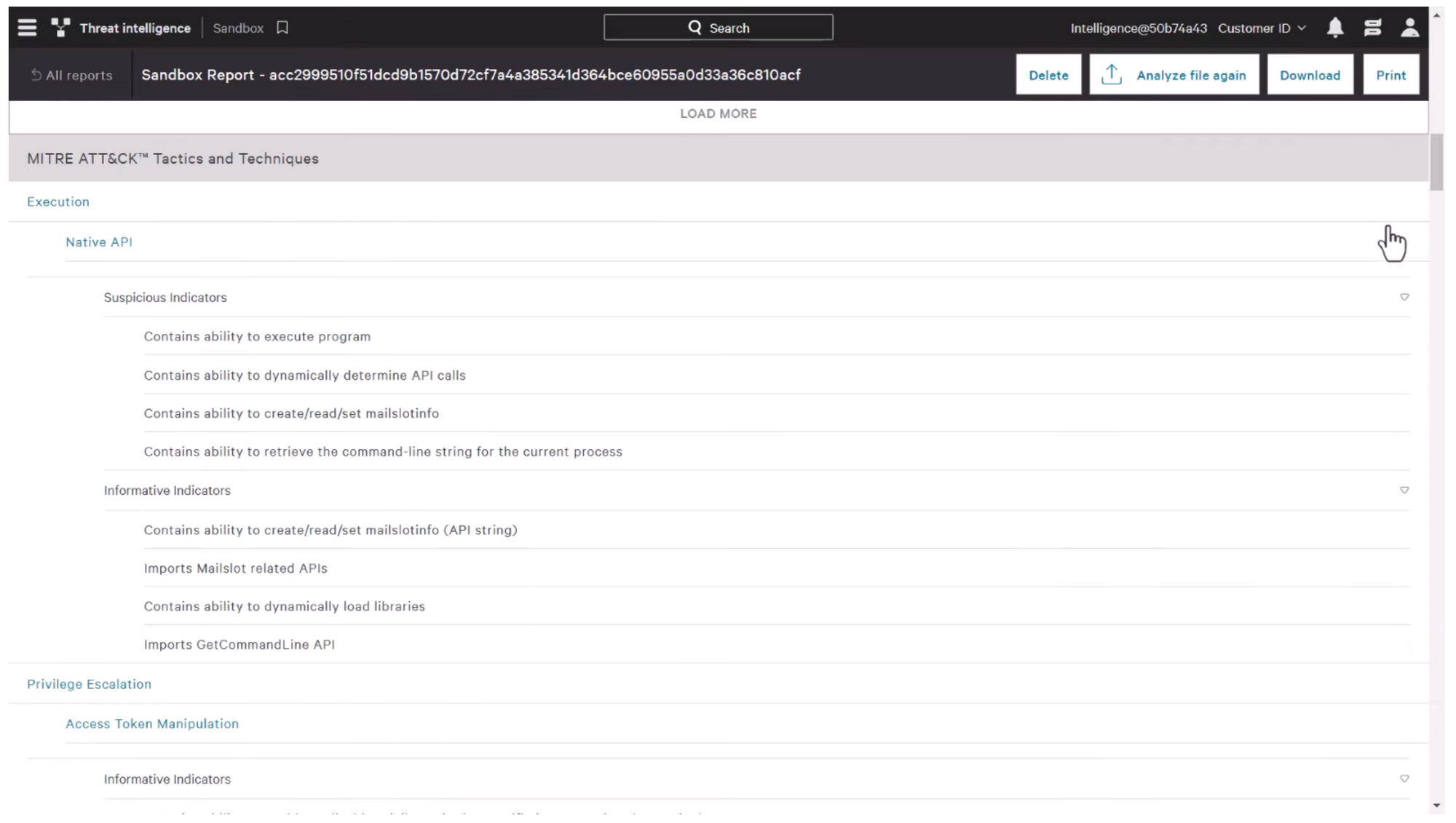
The MITRE ATT&CK mapping will give additional context to the file's behaviour and its relationship with known threat actor techniques, tactics and procedures.
SOC Prime
SOCPrime offers a variety of tools and services that can help improve the threat detection and response capabilities for organizations. The platform offers a wide range of tools and services to help organizations improve their threat detection and response capabilities. Content is created and curated by a network of global cybersecurity professionals to ensure that it is relevant and up-to date.S OCPrime also offers an array of automation tools to help organizations automate detection and remediation, which reduces the time needed to respond to incidents.
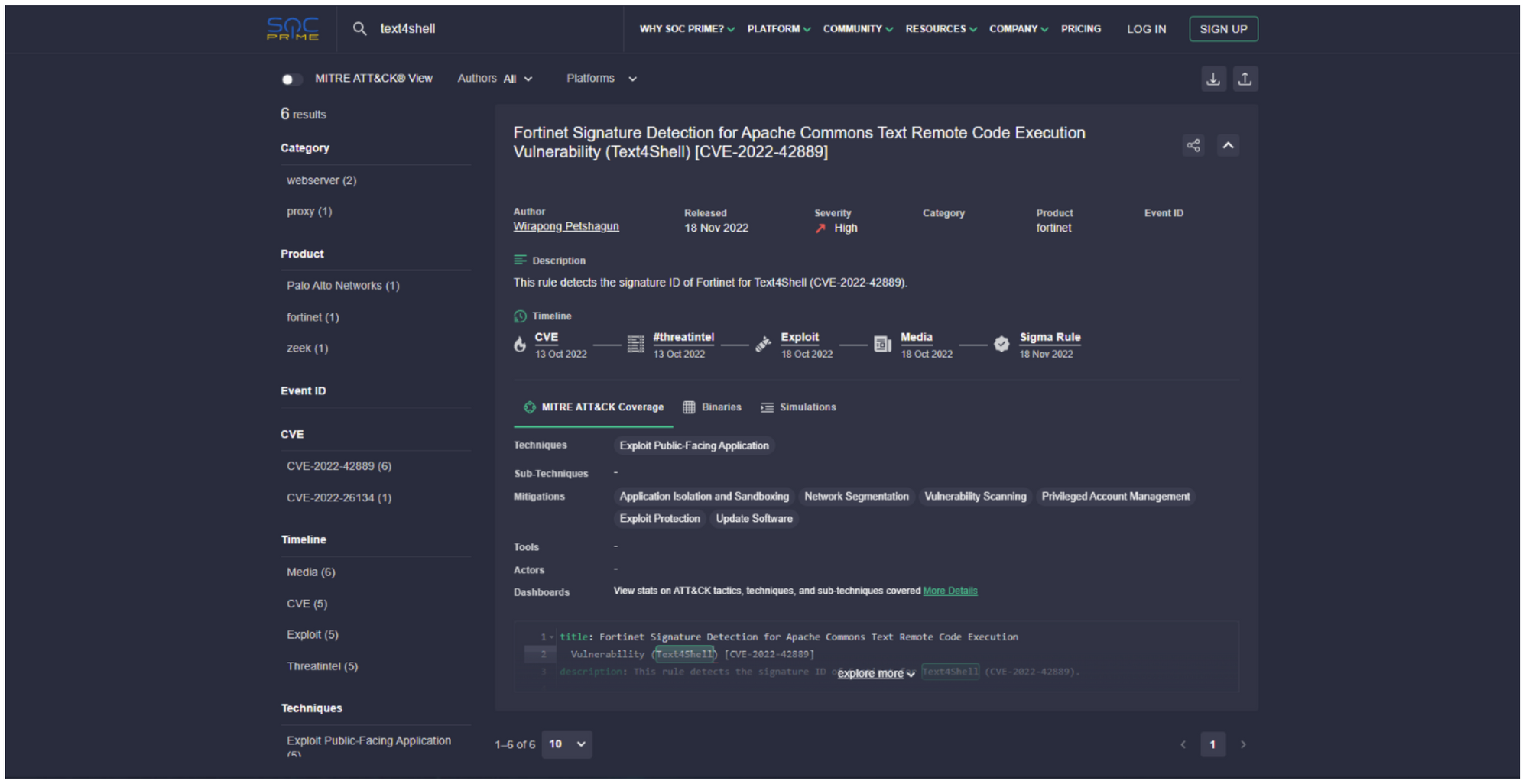
The analysis contains information about the vulnerability or attack identified, including the title, description and CVE identifier. It also shows how an attack is mapped to the MITRE ATT&CK Framework, indicating the tactics and techniques that are used.
The analysis also shows an example of a Sigma rule which can be used to detect or prevent the attack.These details can help security teams develop their defenses to counter known and emerging threats.
Malware Information Sharing Platform (MISP)
MISP is an open source threat intelligence platform that allows organizations to store, share and correlate information on security threats. MISP is a collaborative platform that allows security teams, communities, and organizations to share indicators of compromise, such as malware samples and network traffic patterns.
MISP allows security analysts to be informed of the latest cyber threats and trends by sharing real-time threat intelligence data. MISP offers a variety of APIs for integration with other security platforms and tools, as well as support for various data imports. MISP supports a variety of standards, including STIX and TAXII. It also allows for data sharing across communities and integration with other threat intelligence platforms.
MISP can be installed on-premises in several ways, including using pre-packaged virtual machine, Docker containers or Ansible and Puppet. A Bash script is also available to install MISP on various operating systems such as Ubuntu Kali Linux RHEL and CentOS.
Once the MISP instance has been installed, it is ready for use. The configuration process is simple. For a production environment however, additional steps may be required, such as configuring PGP, mail, authentication, and permissions.
To gather threat data, the first step is to enable the free feeds provided by CIRCL, which can be found in the Sync Actions | List Feeds menu. After enabling the feeds, the MISP instance can begin observing shared and collected events.
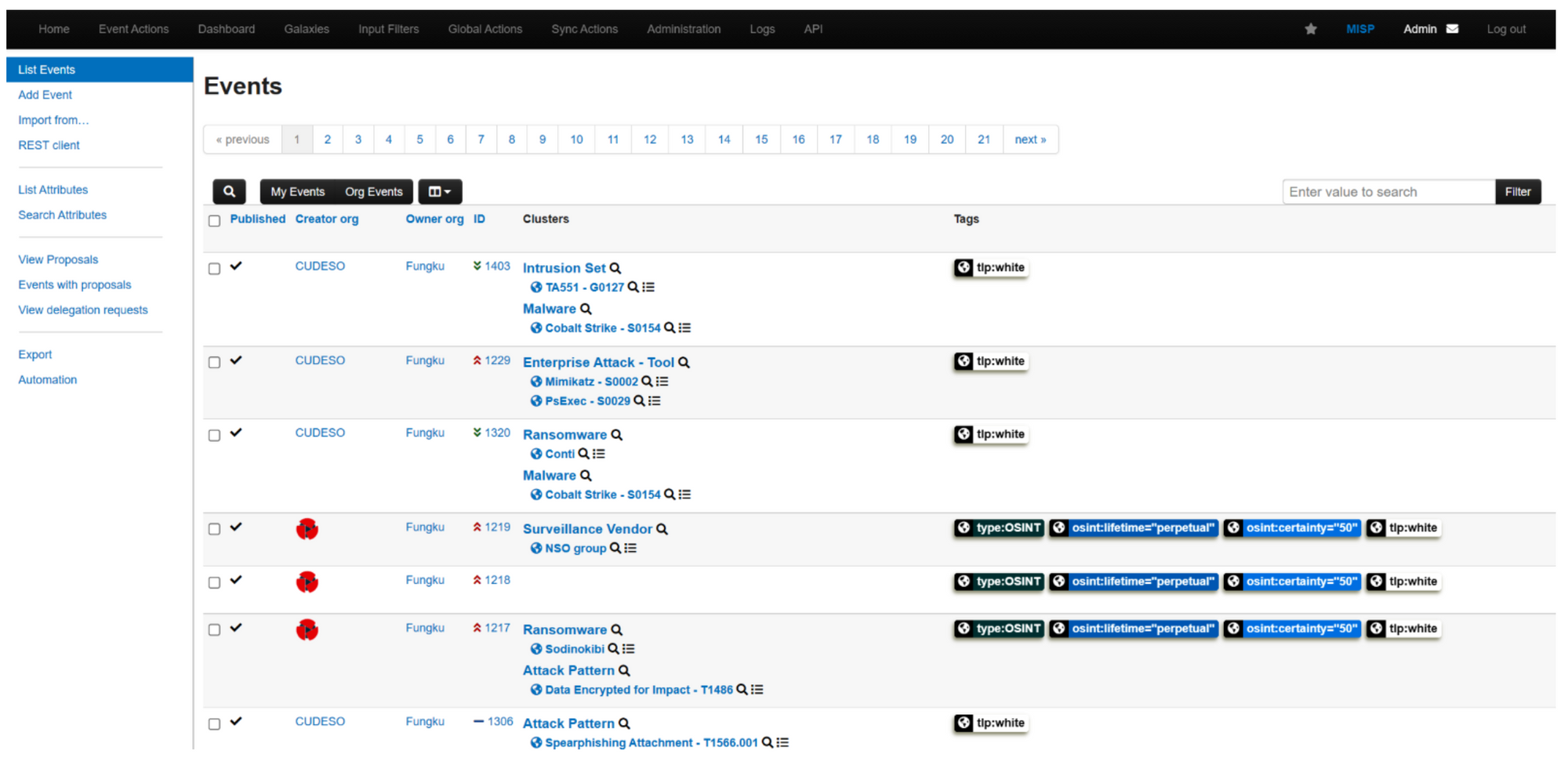
The preceding screenshot shows that events are shared with tags, which can be utilized to search for specific information. For instance, the tlp:white tag is visible, indicating the Traffic Light Protocol. In addition, MISP's Galaxies feature can be used to target relevant data.
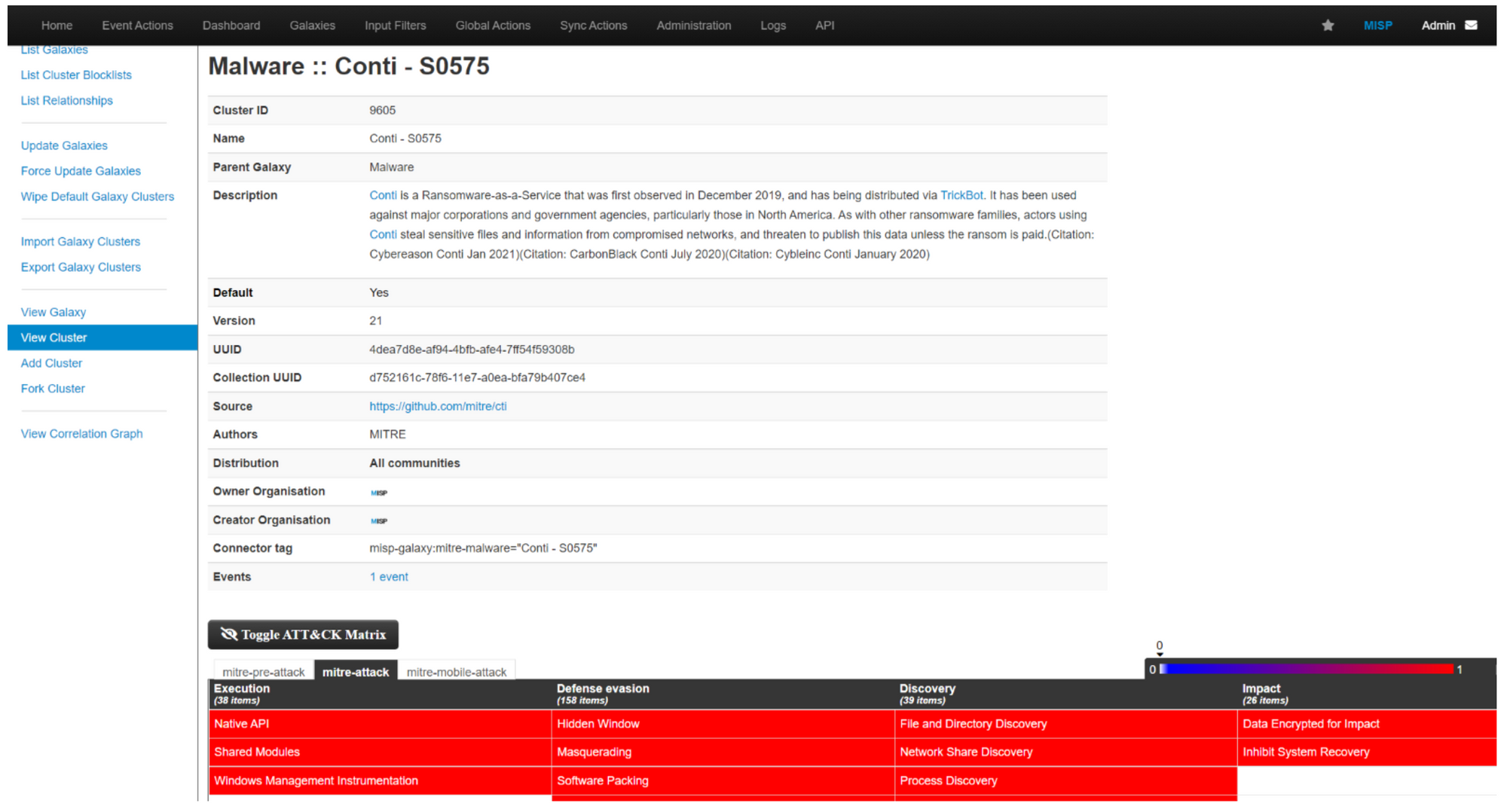
In the above example, the Malware Galaxy was selected and a search was conducted for the Conti ransomware.The malware description was immediately found, along with a MITRE ATT&CK map and several references.This page will display all events related to the malware if they are tagged correctly by those who have shared them.The main problem with this solution is the fact that organizations have to use the correct tags whenever they share events related threats.
OpenCTI
OpenCTI is a platform that allows you to manage and share cyber threat intelligence. It offers a common language for analysts and tools to help them collect, enrich and share threat data in a structured way. OpenCTI provides a comprehensive data structure that integrates data from various sources, including indicators of compromise, incidents, campaigns and threat actors. The tool also includes a powerful search, visualization tools and a flexible API REST for easy integration.
OpenCTI was designed to facilitate collaboration and information exchange between teams, organisations, and across sectors and industries. OpenCTI's community-driven approach to development and open-source licensing make it an affordable and accessible solution for all organizations looking to improve their threat intelligence capabilities.
The installation process is straightforward and you can find the project website at https://www.opencti.io/en/.
OpenCTI was designed specifically to work with STIX. This allows you to focus on data related to a country, industry or threat actor.
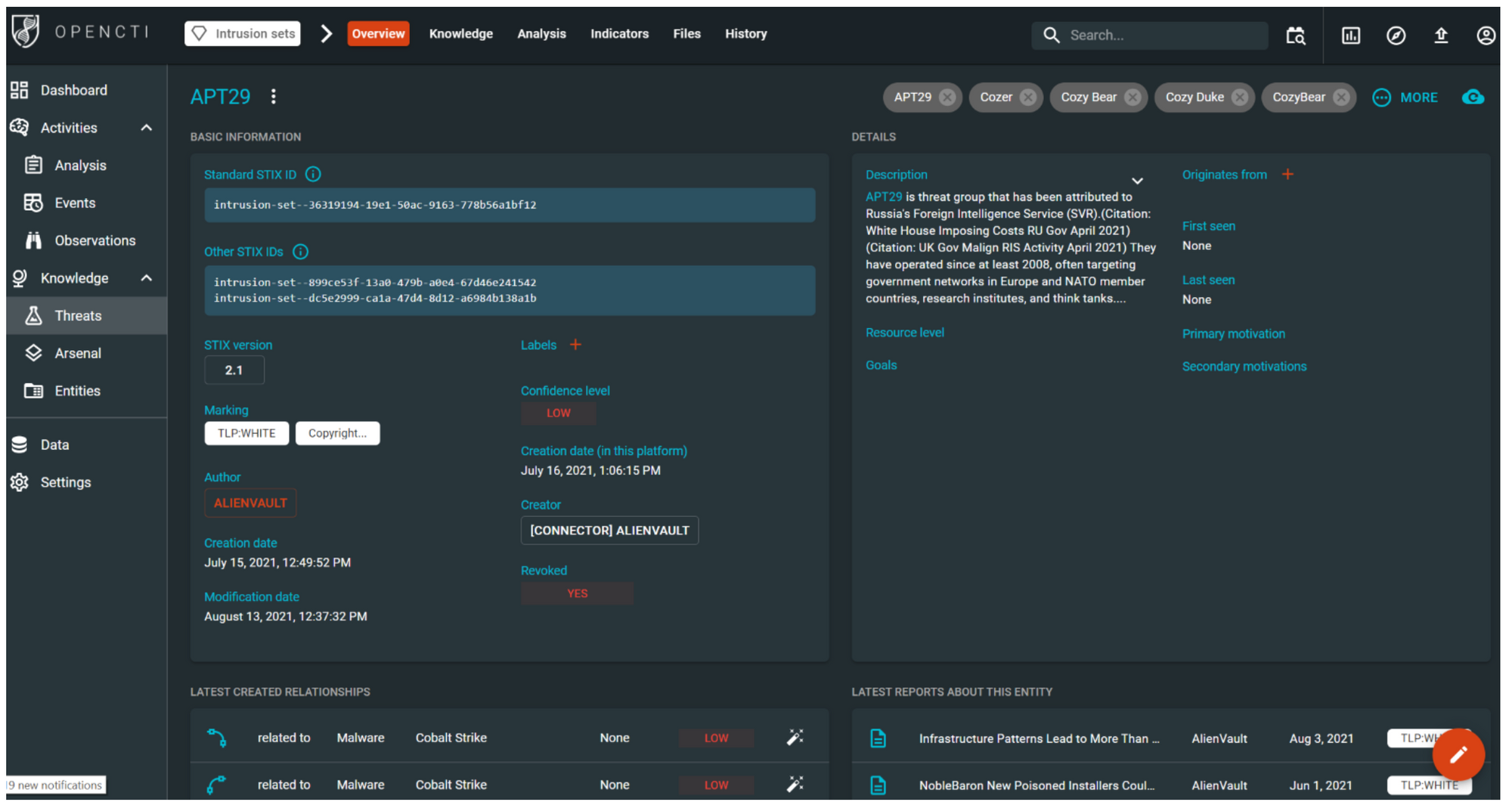
The screenshot above shows the Threats view in OpenCTI. It displays data relating to APT29's intrusion set.This screenshot shows us the other names that are associated with this threat actor. For example, Cozy Bear.The screenshot also includes a description, as well as various metadata and recent reports about this entity.
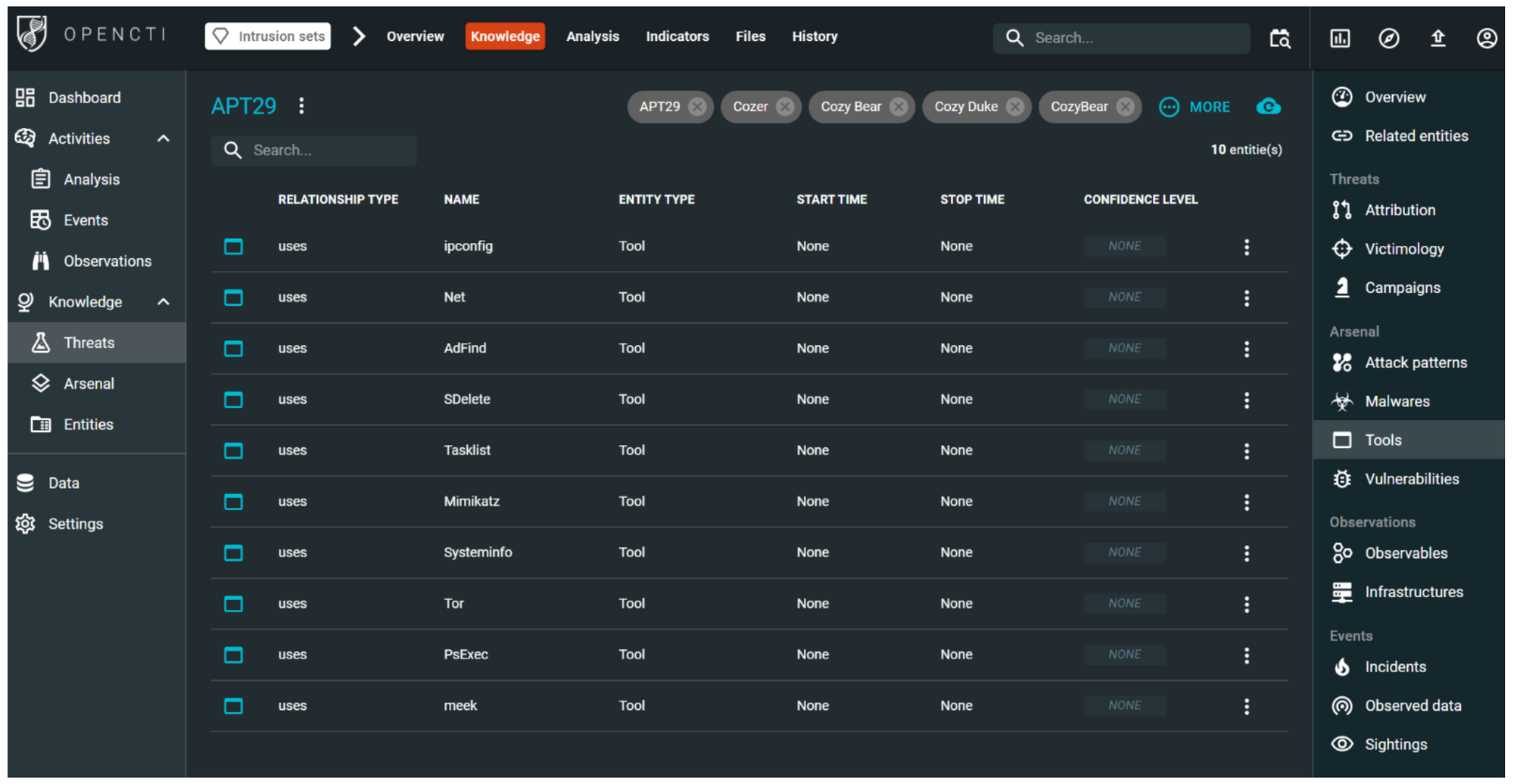
Assuming we want to gain insight into the tools used by this threat actor, rather than the malware, we can navigate to the Knowledge | Tools view. Here, we can identify any connections between the threat actor and specific tools, such as ipconfig, ADFind, or PSExec.
Conclusion
There are other platforms and sources that provide threat intelligence.The above exploration should be of benefit to the IT Security Community, especially for those just entering the threat intelligence world.
References
1. Routin, D., & Rossier, S. T. (2022). Purple Team Strategies. Birmingham: Packt Publishing Ltd.


