Overview
In the ever-changing world of cyber security, staying up to date on the latest techniques used by cyber attackers to infiltrate systems and steal sensitive data is critical. The MITRE ATT&CK framework and the Suricata ET Open Ruleset are two widely used frameworks in the industry for tracking and analyzing these techniques. In this article, we aim to give an overview of these two frameworks and the relationship between them.
MITRE ATT&CK is a comprehensive knowledge base of cyber-attack techniques and tactics used by adversaries. It’s a globally accessible resource for the cybersecurity community and is continuously updated with the latest techniques. There are 67 MITRE techniques that have Network Traffic as the detection data source.
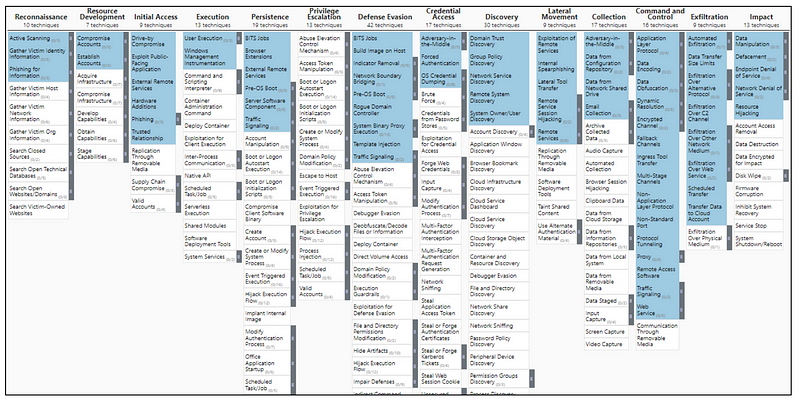
Suricata is an open-source intrusion detection and prevention system that uses signature-based rules to identify malicious activity on a network. The Suricata ET Open Ruleset used in this report is as of February 7th, 2023, for Suricata version 6. It has a total of 32,806 signatures, but only 2,878 of these signatures have metadata tags related to the MITRE tactics and techniques.
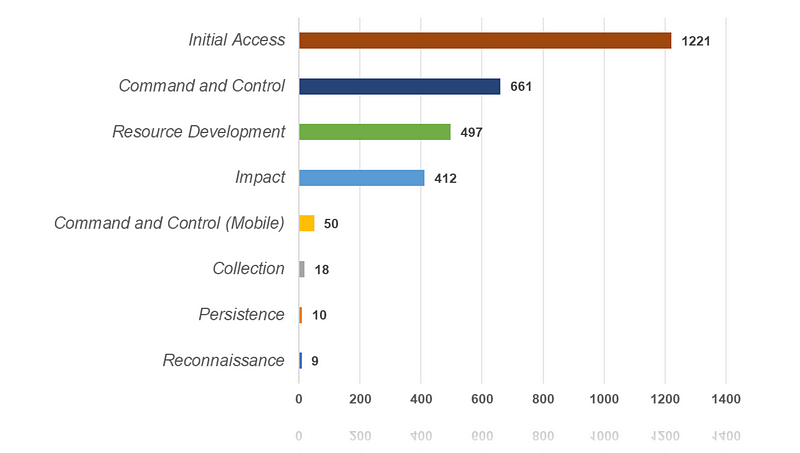
Out of the 2,878 signatures in the ET Open Ruleset that have MITRE-related metadata, there are 8 tactics and 11 techniques that have been identified and mapped to MITRE techniques. These tactics, along with their corresponding percentage of occurrence, and relevant URLs, are listed below:
- Initial Access (https://attack.mitre.org/tactics/TA0001) — 42.4% (1,221)
- Command and Control (https://attack.mitre.org/tactics/TA0011) — 23% (661)
- Resource Development (https://attack.mitre.org/tactics/TA0042) — 17.3% (497)
- Impact (https://attack.mitre.org/tactics/TA0040) — 14.3% (412)
- Command and Control (Mobile) (https://attack.mitre.org/tactics/TA0037) — 1.7% (50)
- Collection (https://attack.mitre.org/tactics/TA0009) — 0.6% (18)
- Persistence (https://attack.mitre.org/techniques/T1001https://attack.mitre.org/tactics/TA0003) — 0.3% (10)
- Reconnaissance (https://attack.mitre.org/tactics/TA0043) — 0.3% (9)
Below are the listed techniques with their corresponding occurrence percentage and relevant URL:
- Phishing (https://attack.mitre.org/techniques/T1566) — 42.4% (1,221)
- Exfiltration Over C2 Channel (https://attack.mitre.org/techniques/T1041) — 18.4% (532)
- Develop Capabilities (https://attack.mitre.org/techniques/T1587) — 15.9% (457)
- Data Encrypted for Impact (https://attack.mitre.org/techniques/T1486) — 12.6% (363)
- Data Obfuscation (https://attack.mitre.org/techniques/T1001) — 3.8% (110)
- Application Layer Protocol (https://attack.mitre.org/techniques/T1071) — 1.9% (56)
- Resource Hijacking (https://attack.mitre.org/techniques/T1496) — 1.7% (49)
- Data from Local System (https://attack.mitre.org/techniques/T1005) — 0.6% (18)
- Encrypted Channel (https://attack.mitre.org/techniques/T1573) — 0.5% (13)
- Server Software Component (https://attack.mitre.org/techniques/T1505) — 0.3% (10)
- Search Open Websites/Domains (https://attack.mitre.org/techniques/T1593) — 0.3% (9)
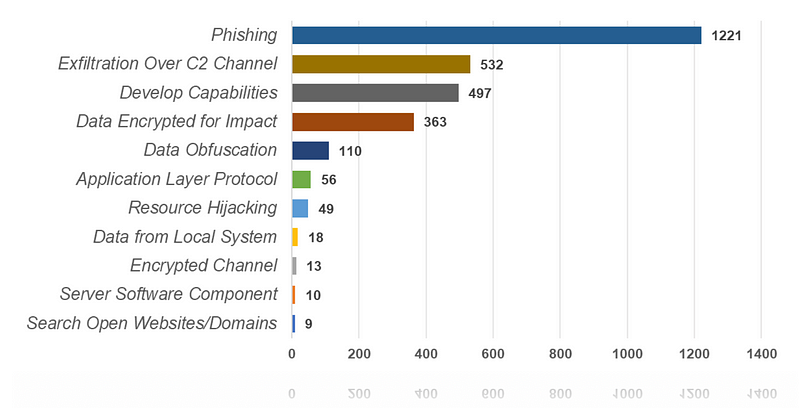
It is worth noting that the techniques Develop Capabilities, Data Encrypted for Impact, Data from Local System, and Search Open Websites/Domains do not rely on Network Traffic as their detection data source. This highlights the importance of considering alternative sources of information when identifying cyber-attacks.
While most of the signatures in the ET Open Ruleset that are tagged with metadata for MITRE tactics and techniques use conventional keywords like “mitre_technique_id” or “mitre_technique_name,” some use non-standard “tag” keywords instead. This can make it more difficult to accurately map the signatures to MITRE techniques and tactics and highlights the need for standardization in metadata tagging across the security community.
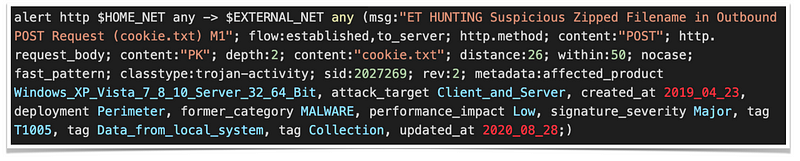
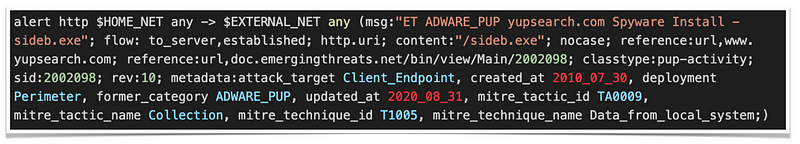
The report has identified several signatures that require correction in their tagging based on the technique they represent.
In order to improve the accuracy of mapping and to assist security teams in identifying the types of attacks they may face, we conclude that all signatures tagged for the Command and Control (Mobile) tactic, and some of those tagged for the Exfiltration Over C2 Channel technique — should be instead tagged for the Exfiltration tactic.
The MITRE ATT&CK framework and Suricata ET Open Ruleset play a crucial role in monitoring and examining cyber-attack techniques. The correlation between Suricata signatures and MITRE techniques offers a deeper understanding of the attack vectors that can be identified by using the ET Open Ruleset.
However, there is more potential room for further improvement in the completeness of the ruleset and the precision of the mapping.
Future reports will delve deeper into these areas for more comprehensive analysis and findings.