Background
In our Honeypot we've observed that there have been numerous DNS queries for specific domains (peacecorps.com, and pizzeo.com) over the past few days. It is likely a DNS Amplification Attack.
Zeek is used to analyze traffic coming from our honeypot. Zeek didn't recognize this event as an attacker with the default configuration (no entries in the Notice.log).
Solution
There are several options to have Zeek send an alert when the event occurs. We chose to create a Zeek custom script as our solution. This script will log an event in the notice log each time DNS traffic is used to query pizzaseo.com or peacecorps.gov.
We begin by declaring the name of our module. This name will be displayed in the notification log as the category of the message. This is similar to the "package statement" in Java code.
module DDosAttacks;After that, we also need to make sure that Zeek’s DNS Module have been loaded. This is somewhat similar to “import” statement in Java coding.
@load base/protocols/dnsThen, you will need to ensure that Zeek's Domain Name System Module has been loaded. This is similar to the "import" statement used in Java code.
redef enum Notice::Type += {
DNSDDoSAmplification
};Next, we will create the Notification Framework function.The function will require input for the connection and query string DNS.The notification framework will be sent if the query contains Pizzaseo.com and Peacecorps.gov.
function generate_ddos_notice(c: connection, query: string) {
local query1: string = strip(query);
if (query1 == "peacecorps.gov" || query1 == "pizzaseo.com") {
NOTICE([$note = DNSDDoSAmplification, $msg = fmt("Possible DNS DDoS Amplification Attack"), $conn = c,$uid = c$uid]);
}
}We need to determine which event we will use.We need to identify which Zeek events are appropriate for DNS traffic.Using the link for reference, we chose to use "dns_request", and "dns_query_reply".The function that we created earlier will be called by the event.
event dns_request(c: connection, msg: dns_msg, query: string, qtype: count, qclass: count, original_query: string) {
generate_ddos_notice(c, query);
}
event dns_query_reply(c: connection, msg: dns_msg, query: string, qtype: count, qclass: count, original_query: string) {
generate_ddos_notice(c, query);
}Safe the Zeek script and do not forget to load it up in your local Zeek configuration. To test this script, you can use the pcap/trace data from this blog. Just run below command, and then check the resulting notice.log.
zeek -Cr <pcap_file> localThe complete script is available in the gist below.You can modify the script as you need to. Please let us know if you have any suggestions for improvement in the comments section.
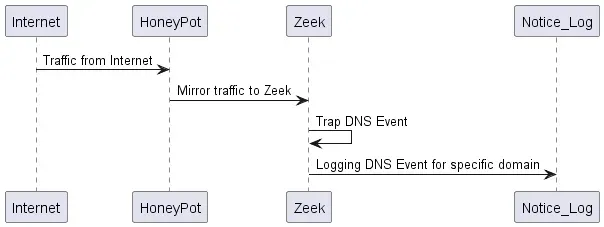
The overall flow of the data is captured in the sequence diagram below.
Remarks
I hope that the explanation above is sufficient for starting to create attack detection script in Zeek.
References and related articles







